Something that’s come up a few times in the last year for me has been a situation where a NetWorker user has wanted to allow someone to access NetWorker Management Console for the purpose of running reports, but not allow them any administrative access to NetWorker.
It turns out it’s very easy to achieve this, and you actually have a couple of options on the level of NetWorker access they’ll get.
Let’s look first at the minimum requirements – defining a reports only user.
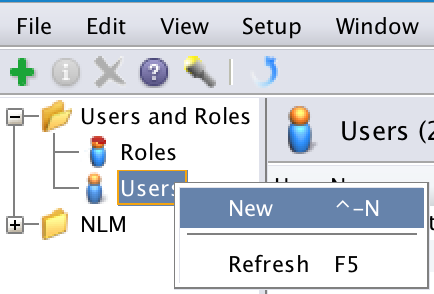
To do that, you first go into NetWorker Management Console as an administrative user, and go across to the Setup pane.
You’ll then create a new user account:
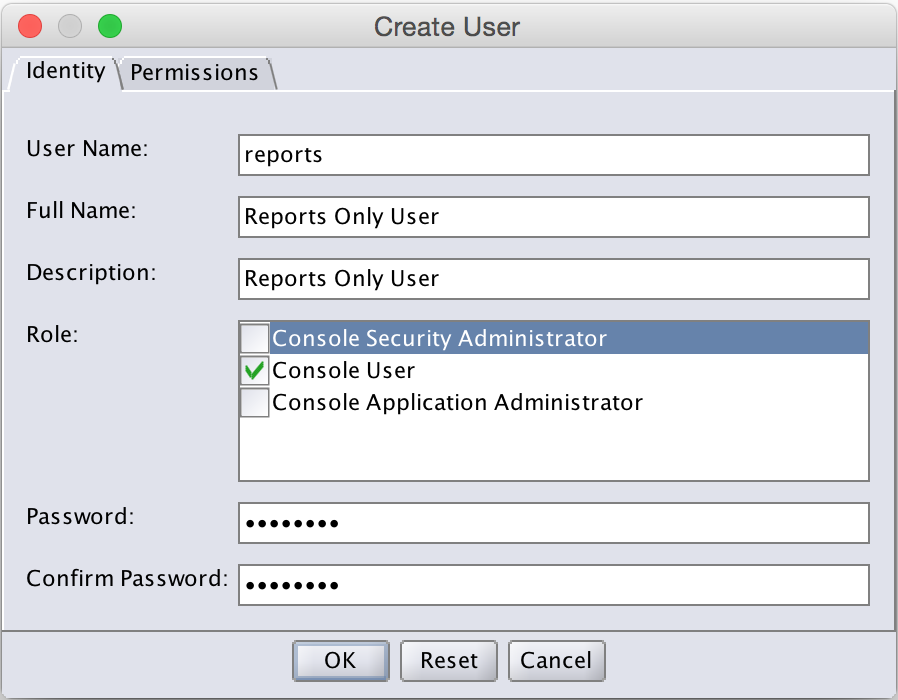
Within the Create User dialog, be certain to only select Console User as the role:
At this point, you’ve successfully created a user account that can run NMC reports, but can’t administer the NetWorker server.
However, you’re then faced with a decision. Do you want a reports-only user that can “look but don’t touch”, or do you want a reports-only user that can’t view any of the NetWorker configuration (or at least, anything other than can be ascertained by the reports themselves)?
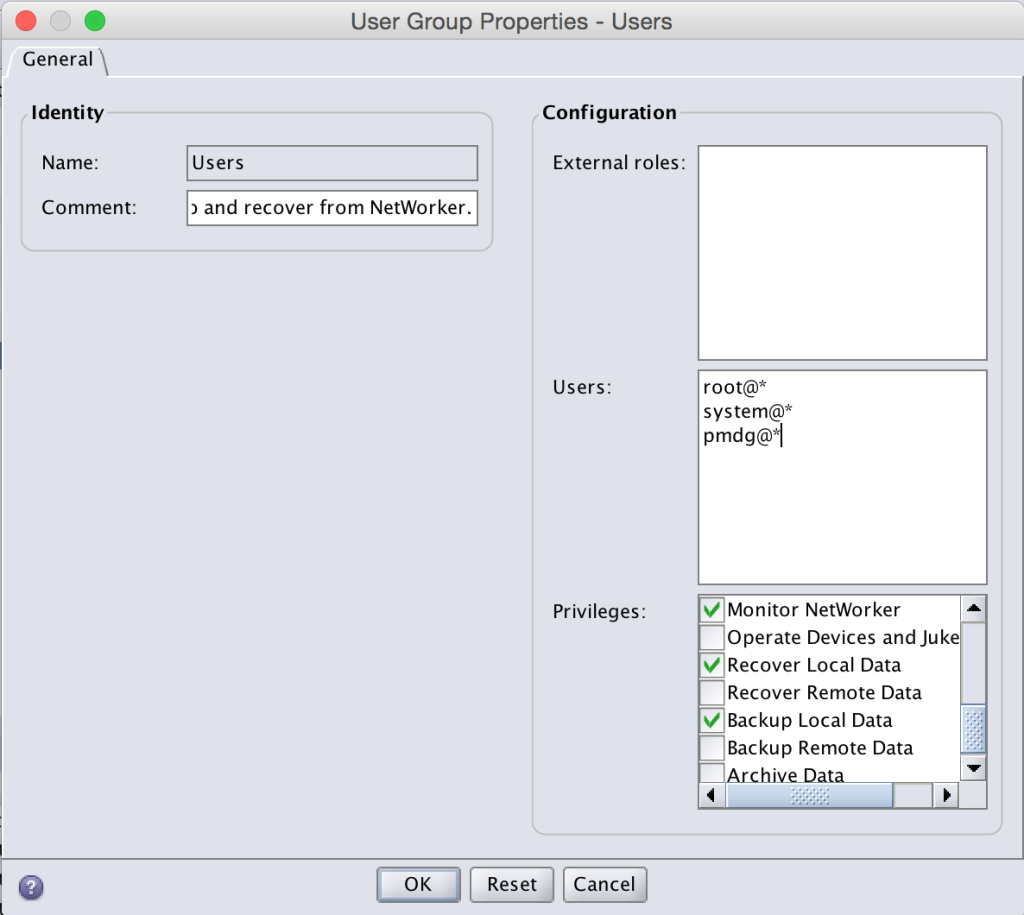
If you want your reports user to be able to run reports and you’re not fussed about the user being able to view the majority of your NetWorker configuration, you’re done at this point. If however your organisation has a higher security focus, you may need to look at adjusting the basic Users NetWorker user group. If you’re familiar with it, you’ll know this has the following configuration: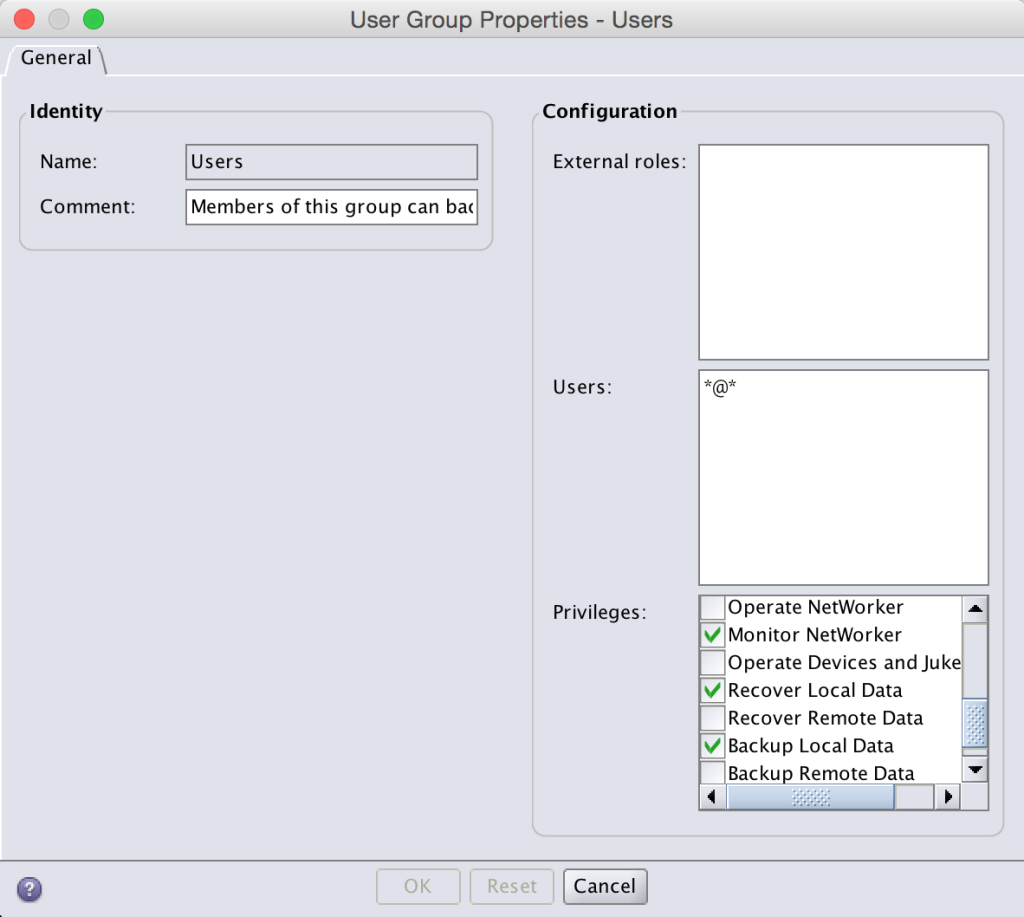
This usergroup in the default configuration allows any user in the NetWorker datazone to:
- Monitor NetWorker
- Recover Local Data
- Backup Local Data
The key there is any user – *@*. Normally you want this to be set to *@*, but if you’re a particularly security focused organisation you might want to tighten this down to only those users and system accounts authorised to perform recoveries. The same principle applies here. Let’s say I didn’t want the reports user to see any of the NetWorker configuration, but I did want any root, system or pmdg user in the environment to still have that basic functionality. I could change the Users usergroup to the following:
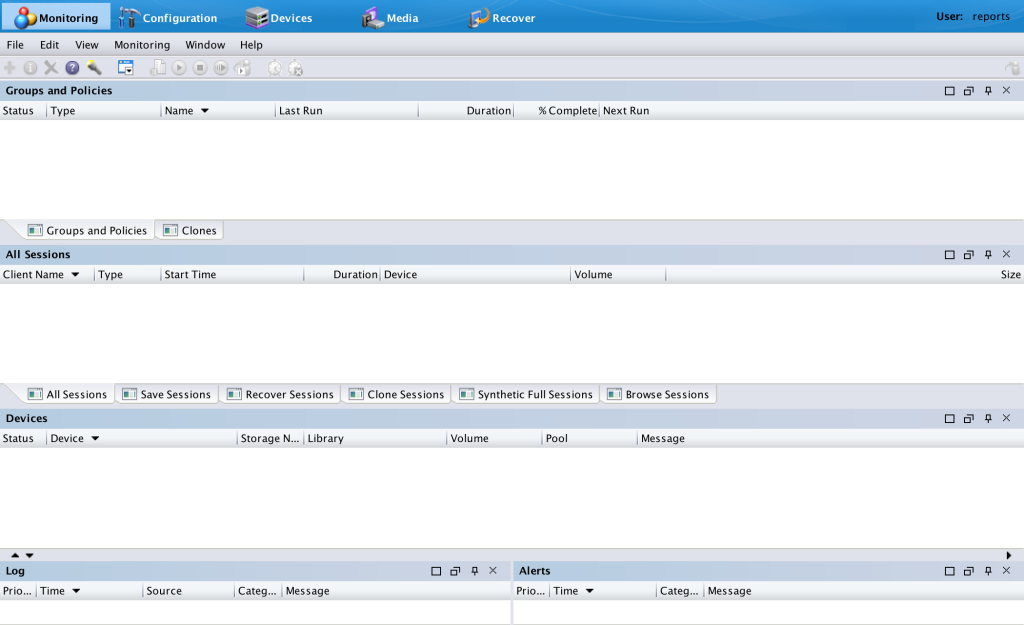
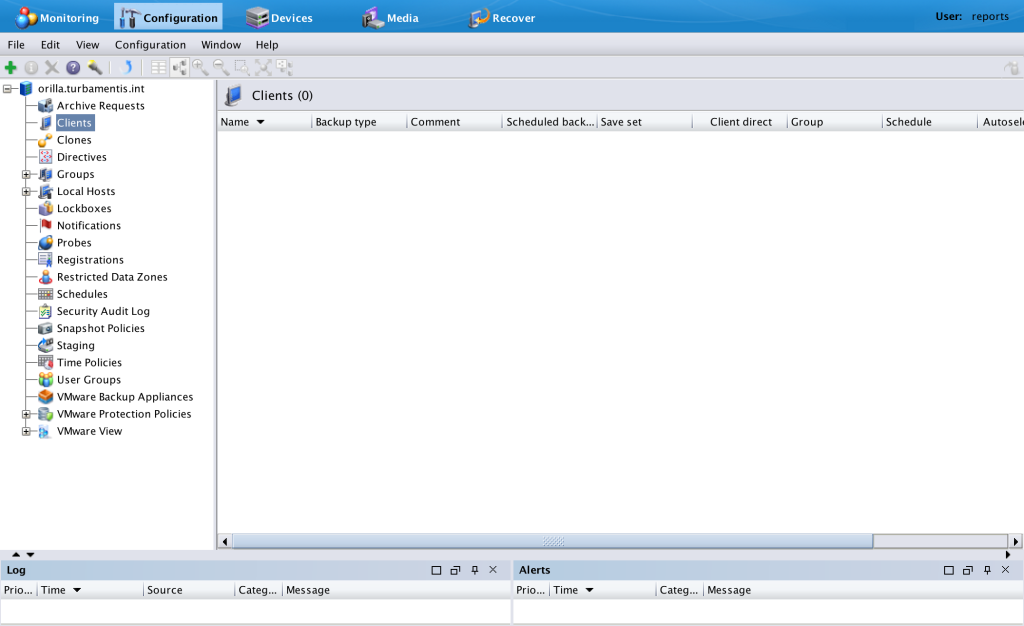
With this usergroup modified, logging in as the reports user will show a very blank NMC monitoring tab:
Similarly, the client list (as an example) will be quite empty too:
Now, it’s worth mentioning there are is a key caveat you should consider here – some modules may be designed in anticipation that the executing user for the backup or recovery (usually an application user with sufficient privileges) will at least be a member of the Users usergroup. So if you tighten the security against your reports user to this level, you’ll need to be prepared to increase the steps in your application onboarding processes to ensure those accounts are added to an appropriate usergroup (or a new usergroup).
But in terms of creating a reports user that’s not privileged to control NetWorker, it’s as easy as the steps above.