While NetWorker 9 went DA at the end of September and is seeing healthy uptake around the world, NetWorker 8.2 is still getting updates.
Released a couple of weeks ago, NetWorker 8.2 SP2 includes a slew of changes. While undoubtedly NetWorker 9 will be seeing the majority of new-feature development henceforth, that’s not to say that NetWorker 8.2 won’t get refinements as required and planned.
Some of the changes and updates to NetWorker with the 8.2 service pack 2 release include:
- Support for JRE 1.8/Java 8 – You can now run the NMC interface using Java 8
- Reduced name resolution checking – NetWorker still requires name resolution (of some form), as you’d hope to see in an enterprise product, but there’s been a refinement to the times NetWorker will perform name resolution. Thus, if your DNS service is particularly slow or experiencing faults, NetWorker should not be as impacted as before*.
- Automated checks:
- Peer Information
- Storage nodes
- Usergroup hosts
- Maximum device limit can be increased to 1024. If you’ve got a big datazone that’s running at or near 750 devices, you can now increase the maximum device count to 1024.
- DDBoost Library upgrade – NetWorker 8.2 SP2 uses libDDBoost 3.0.3.0.
It’s the automated checks I want to spend a little time on. As a NetWorker admin or implementation consultant I would have killed for these sorts of tests; and indeed, I even wrote some scripts which did some similar things. If you’ve not used them before, you should have a look at some of the tests previously added (here and here).
The new options though continue to enhance that automated checking and will be a boon for any NetWorker administrator.
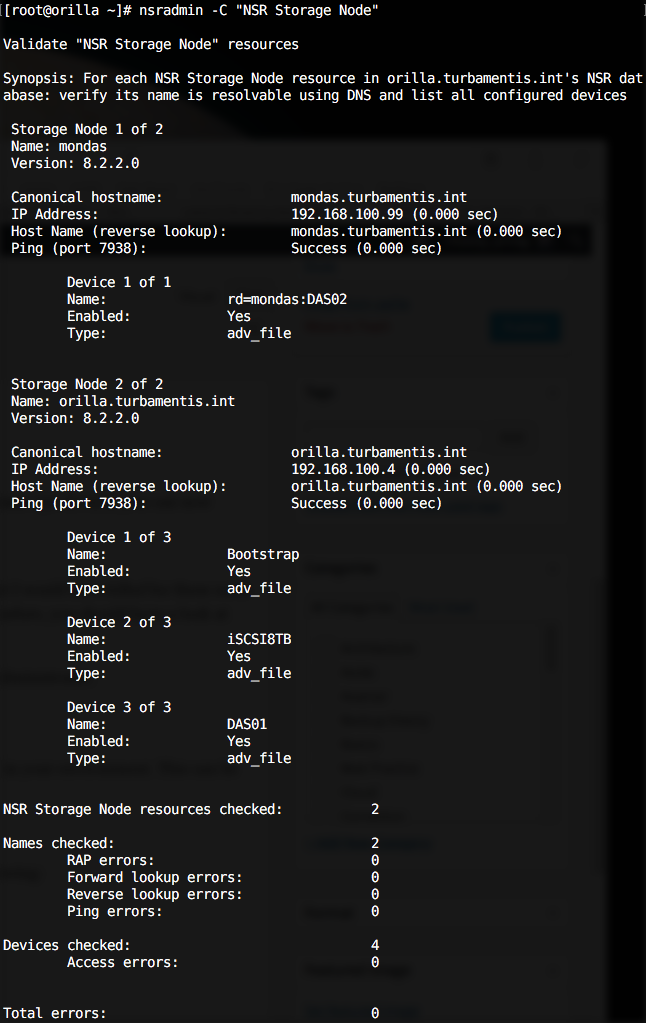
Storage Node Checking
The first new option I’d like to show you is the option to automatically check the status of all the storage nodes in your environment. This can be performed by executing the command:
# nsradmin -C "NSR Storage Node"
The output from this will obviously be dependent on your environment. In my lab I get output such as the following:
So for each storage node, you get name resolution checking for the storage node (forward and reverse), as well as a dump of the devices attached to the storage node. If you have an environment that has a mesh of Data Domain device mounts, or dynamic drive sharing/library sharing, this will make getting a very quick overview of devices a piece of cake.
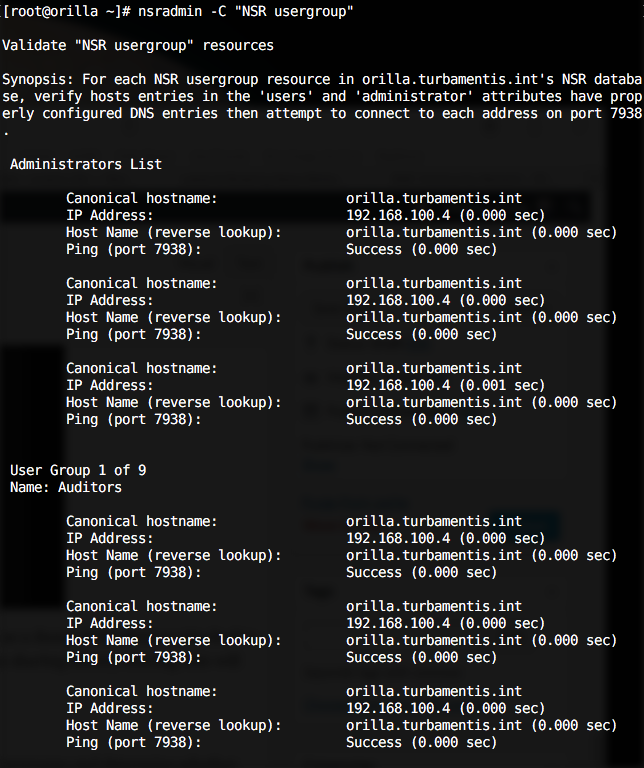
Usergroup Host Checking
As a means of more tightly checking security options, you can now query the hosts referenced in NetWorker Usergroups and determine whether they can be correctly resolved and reached. This command is run as follows:
# nsradmin -C "NSR usergroup"
And the output (for my system) looks a bit like the following:
(Note that it will check the referenced hosts for each user specified for that host.)
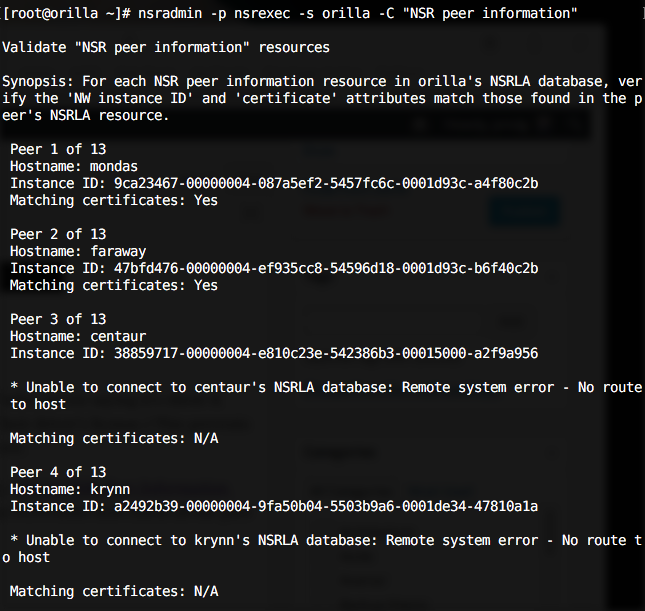
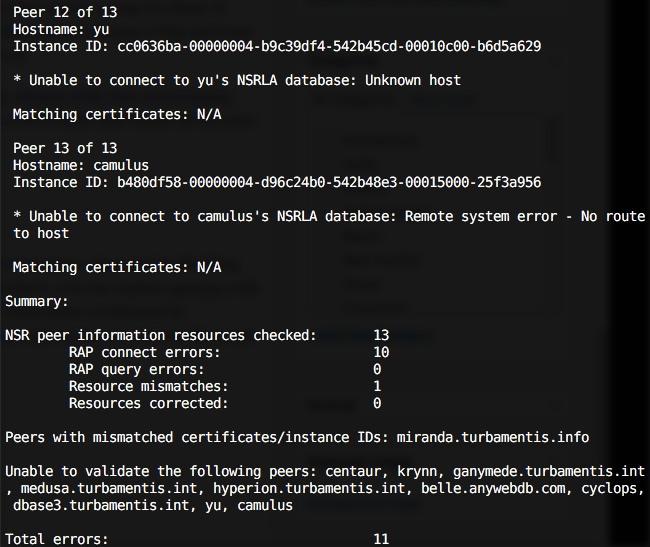
NSR Peer Information
NetWorker uses peer information – generated certificates – to validate that a host which connects to the NetWorker server saying it’s client-X really can prove it’s client-X. (It’s like the difference between asking someone their name and asking them for their driver’s license.) This prevents hosts from attaching to your network, impersonating one of your servers, and then recovering data for that server.
Sometimes if things radically change on a client that peer information may get outdated and require refreshing. (Fixing NSR Peer Information Errors remains the most accessed post on my blog.) Now you can use the automated checking routine to have a NetWorker host check all the peer certificates in its local client resource database.
The command in this case has to reference the client daemon, and so becomes:
# nsradmin -p nsrexec -s clientName -C "NSR peer information"
If you run it from the NetWorker server, for the NetWorker server, the clientName in the above becomes the server name, since you’re checking the client resource for the server. Note if you’re feeling particularly old-school (like I do all the time with NetWorker), you can replace nsrexec with 390113 in the above as well. This is actually also a good way of checking client connectivity, since we verify any local client certificates by comparing the locally cached certificate against the certificated stored on each client. (Given I’m running this on a lab server, it’s reasonable to see some timeouts and errors.)
For my lab, the results look like the following:
…
If you intend to wait a while (or until it hits GA) before you upgrade to NetWorker 9, I’d heartily recommend upgrading to NetWorker 8.2 SP2 if for no other reason than the incredibly useful automated checks that have been introduced.
—
* If your DNS/name resolution is improperly configured or faulty, I’d suggest it should be dealt with quickly.

It should probably be noted that the 8.2SP2 upgrade for VBA has been pulled – Unfortunately, not before we carried out our upgrade and found all our virtual backups were failing!
We ended up rolling back before EMC sent us through a fix (https://support.emc.com/kb/208835) – but worth keeping in mind for any pending upgrades…
(Thanks for the excellent blog, I’m a relative newcomer to Networker and it’s been invaluable – particularly your upgrade guides, but even stuff as simple as restarting the right services.)