Having just finished the excellent Dickinson series on Apple TV+, I keep getting one of Emily Dickinson’s most famous refrains rolling around in my head:
Because I could not stop for Death –
Because I could not stop for Death, Emily Dickinson.
He kindly stopped for me –
The Carriage held but just Ourselves –
And Immortality.
Now, I’m not suggesting that Emily Dickinson was thinking about the public cloud when she wrote arguably her most famous poem1, but like “don’t run with scissors”, I think her poem also at least partly reflects on running too fast to an objective – so much so that you don’t notice the risks. 2

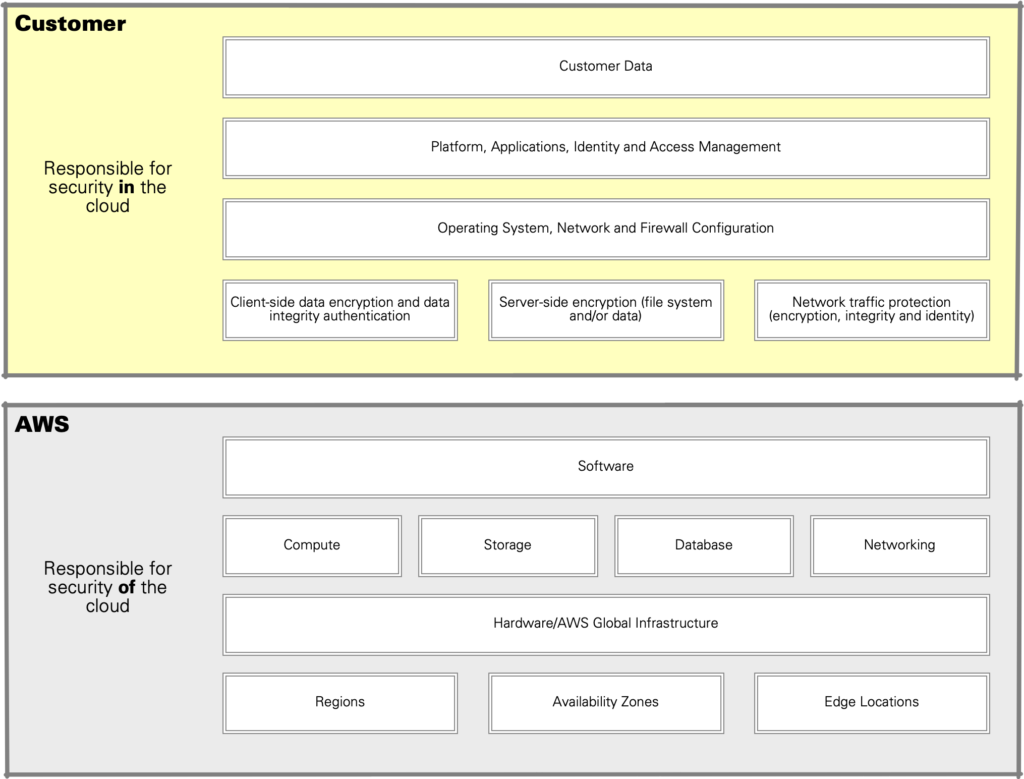
If you’re operating in the public cloud, you should be very much aware of the shared responsibility model:
I’ve said for a while that your backup environment has to be secured to the same level of paranoia as your most mission-critical systems: it represents a terrifying potential attack vector for your entire organisation if unsecured, and also represents an easy target for data breach situations. I.e., why would attackers scour your network for dozens or more systems if they can get access to everything by compromising the backup server?
And we’re now at the point where backup servers running in the public cloud are becoming very attractive to attackers.
Backups are one the most, if not the most, important defense against ransomware, but if not configured properly, attackers will use it against you.
Recently the DoppelPaymer Ransomware operators published on their leak site the Admin user name and password for a non-paying victim’s Veeam backup software.
Ransomware Attackers Use Your Cloud Backups Against You, Lawrence Abrams, March 3, 2020. (Bleeping Computer.)
Lawrence Abrams from the above article quoted someone behind the Maze ransomware software as follows:
“Yes, we download them. It is very useful. No need to search for sensitive information, it is definitely contained in backups. If backups in the cloud it is even easier, you just login to cloud and download it from your server, full invisibility to “data breach detection software”. Clouds is about security, right?”
Ibid.
Backups are very useful. Not just to your business, but to people who might attack your business. People who might be looking to hold your business to ransom or exfiltrate your data. Backups in the cloud are “even easier” to get to.
If you don’t secure them properly. Regardless of whether you have backup services in public cloud, on-premises, or both, you have to secure them of course. But in the public cloud, you might have a broader spread of groups involved in the setup and run. Last year, I wrote about how backup servers, poorly secured, represent a significant security threat. I also wrote about how Data Domain is one of the most important pieces of infrastructure that you can deploy to help secure your backup environment, and much of that holds true even in a virtualized or cloud-based environment – so long as the underpinning infrastructure has been suitably secured.
When I was starting in IT, infrastructure was the castle, and security was a moat surrounding it. You had firewalls and DMZs, but everything inside the network was trusted. Over time we’ve matured, but backup servers were often perversely left out of the security model. So we moved away from relying exclusively on the moat to having every door in the castle locked. However, your backup server is the skeleton key that opens any door. If that’s not protected … well, ransomware developers and hackers will love you.
There’s a lot more I have to say about data protection security in the public cloud in Protecting Information Assets and IT Infrastructure in the Cloud, but I think it’s worth ending with a simple statement:
Backups are the keys to your kingdom.
