Introduction
The NetWorker Usage Survey for 2017 ran from December 1, 2017 through to January 31, 2018. Regretfully, participation rates were lower this year than in previous years; ideally the goal is to get more than 100 respondents; this survey saw only 77 respondents, which narrowed the data usability in places.
While previous survey reports have been published as a PDF document, I’m switching to a blog post for this report – I’ll be interested to hear from readers if this makes it more or less usable (or makes no difference).
Survey Results
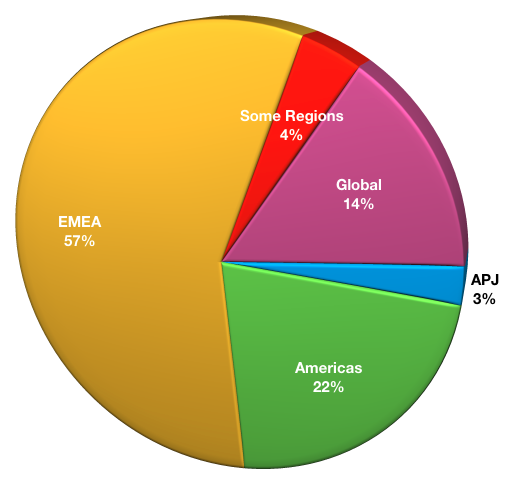
Respondent Location
This question is simply to determine where respondent businesses are located. (The goal from previous surveys was to use this to correlate certain findings against geography.) Due to the lower number of respondents – and particularly, the low number of respondents from APJ – regional correlations will not be drawn in this survey.
- APJ: 2
- Americas: 17
- EMEA: 44
- Some Regions: 2
- Global: 11
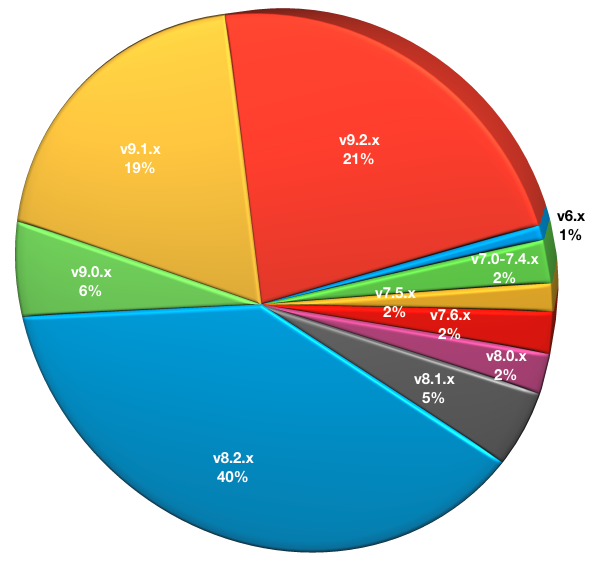
What NetWorker Server Version(s) Are You Running?
Many businesses run more than one backup server, even if they’re both the same product. This may be based on location, function, or security zones. As such, respondents could select more than one NetWorker server version.
- v6.x: 1
- v7.0.x – 7.4.x: 3
- v7.5.x: 2
- v7.6.x: 3
- v8.0.x: 3
- v8.1.x: 6
- v8.2.x: 51
- v9.0.x: 8
- v9.1.x: 25
- v9.2.x: 27
With a reduced subset of the v8.x series remaining in support, it’s worthwhile comparing NetWorker 8.x vs NetWorker 9.x adoption between this survey and the previous:
- NetWorker 8.x:
- 2016 Survey: 74%
- 2017 Survey: 47%
- NetWorker 9.x:
- 2016 Survey: 17%
- 2017 Survey: 46%
Over the past 12 months, the NetWorker 9 series has made significant inroads in adoption. While NetWorker 9 represented a significant configuration change, we are now seeing increased levels of adoption as businesses take advantage of the new functionality (e.g., high speed backup for Exchange systems via NMM with Block Based support, the new vProxy system that replaced VBA, etc.)
How many Datazones do you run?
As mentioned in the previous question, many environments run more than one backup server. This question checks to see how many NetWorker datazones a business is running.
- 1: 34
- 2: 8
- 3: 7
- 4: 4
- 5: 1
- 6-10: 9
- 11-25: 11
- 26-50: 2
- 51-100: 1
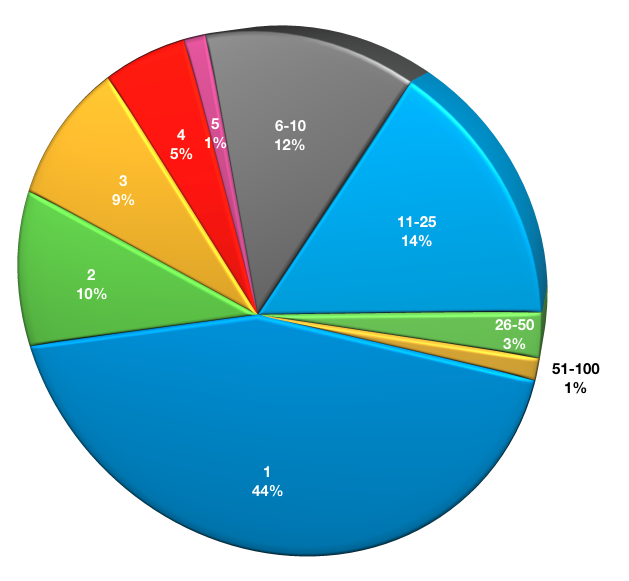
The number of respondents who run only a single datazone continues to sit under 50%; in essence, it is more common than not to have 2 or more NetWorker Datazones. (No doubt flexible licensing models such as capacity based licensing assists on this.)
What is the size of a full backup of everything you’re protecting?
NetWorker is used to protect the smallest through to the biggest environments. Some environments may be as small as just the NetWorker server itself; others may protect thousands of clients and multiple PB of data. This question asked respondents to estimate what the total size of a full backup of everything being protected by NetWorker is.
- No idea: 16
- 1 TB or less: 2
- 1-10 TB: 10
- 51-100 TB: 16
- 101-500 TB: 13
- 501 TB – 1 PB: 6
- 1+ PB to 5 PB: 11
- 5+ PB to 10 PB: 2
- 10+ PB: 1
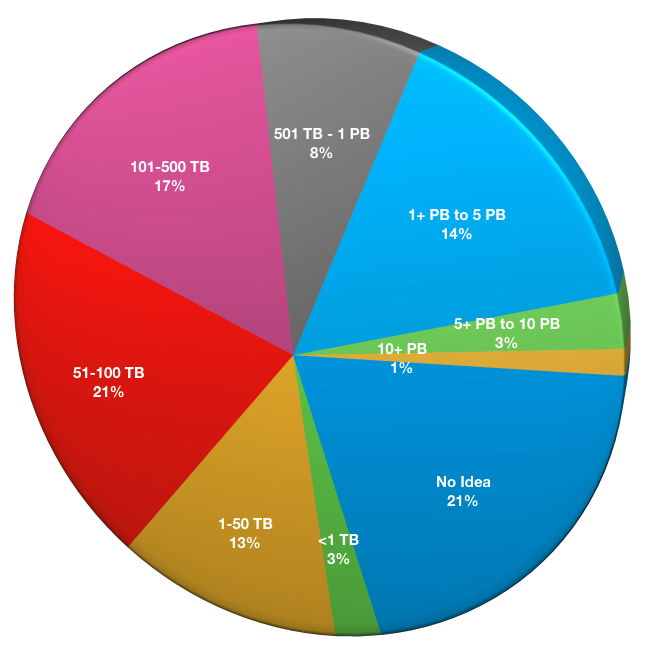
18% of respondents indicated NetWorker protects 1PB or more within their environment; this represents a slight increase compared to previous surveys where this question was asked (2016: 16%, 2015: 17%). In the 2016 survey, 48% of respondents indicated they were backing up 100TB or less within their environments, whereas for the 2017 survey that was 37%, which could be indicative of the effects of data growth within businesses – there’s simply more to protect.
For those respondents who answered with “No idea”, it should be noted that NetWorker 9.2 onwards now includes the capability to provide this estimate. (Refer to my post from last year regarding NetWorker 9.2 Capacity Measurement for details.)
What is the total number of clients you are protecting with NetWorker?
This question seeks to determine the total number of clients being protected (across all datazones) with NetWorker for respondents.
- 1-10: 2
- 11-25: 2
- 25-50: 2
- 51-100: 3
- 101-250: 15
- 251-500: 9
- 501-1000: 12
- 1001-2000: 14
- 2001-5000: 12
- 5001+: 6
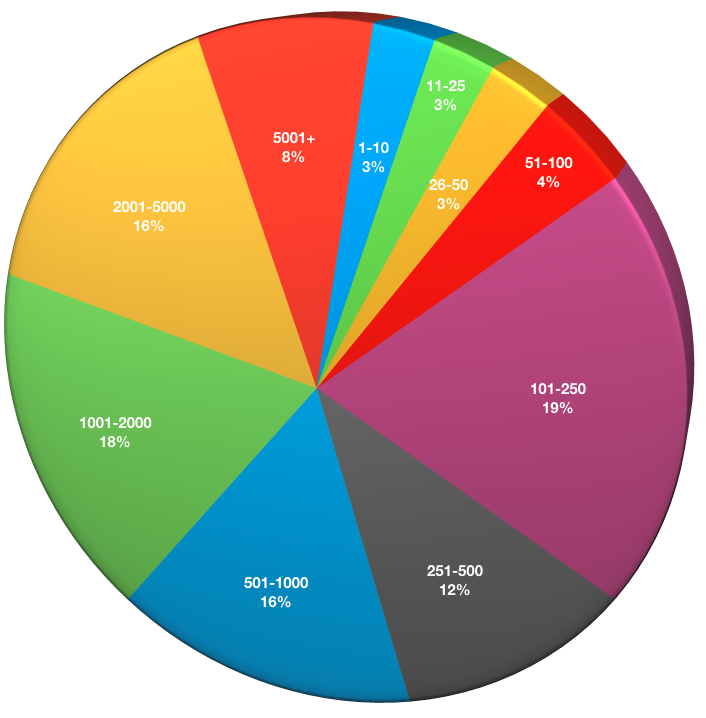
In the 2014 and 2015 surveys, 30% of respondents were protecting 1,001 or more systems using NetWorker; in the 2016 survey that rose to 36%, and for the 2017 survey we see it has risen again, to 42%. Growth is happening not only in the amount of data being protected, but the number of systems being protected – no doubt due to the increasing percentage of virtualisation in many organisations.
NetWorker Server Operating System
While NetWorker 9 reduced the number of platforms the NetWorker server software was supported on to Linux and Windows, there is still room for evaluation of NetWorker server version; non-Windows/Linux platforms are still represented in older versions of the software, and understanding the distribution and type of platforms used in NetWorker 9.x installs is still useful.
- Linux (Free): 12
- Linux (Paid): 39
- Windows 2008/R2: 18
- Windows 2012/R2: 28
- Windows 2016: 4
- AIX: 4
- HPUX: 1
- Solaris: 8
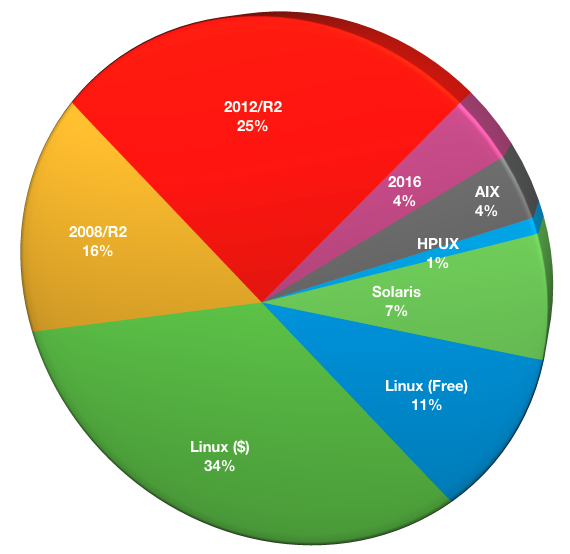
(It is noted the survey erroneously left off options for older versions of Windows.)
If we evaluate simply based on platform type (Windows, Linux and Legacy Unix), the breakdown is as follows:
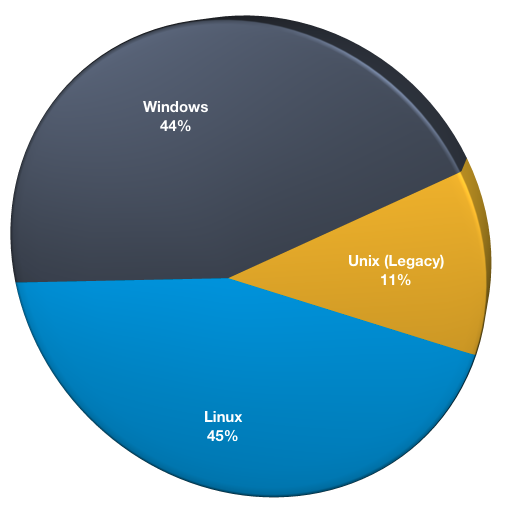
As you would expect to see over time, given the increased adoption of v9.x (supporting only Linux or Windows as the operating system for the NetWorker server), we are seeing a decline in the overall use of Legacy Unix platforms for the server. (Last year’s survey saw legacy Unix as occupying 19% of server installs.)
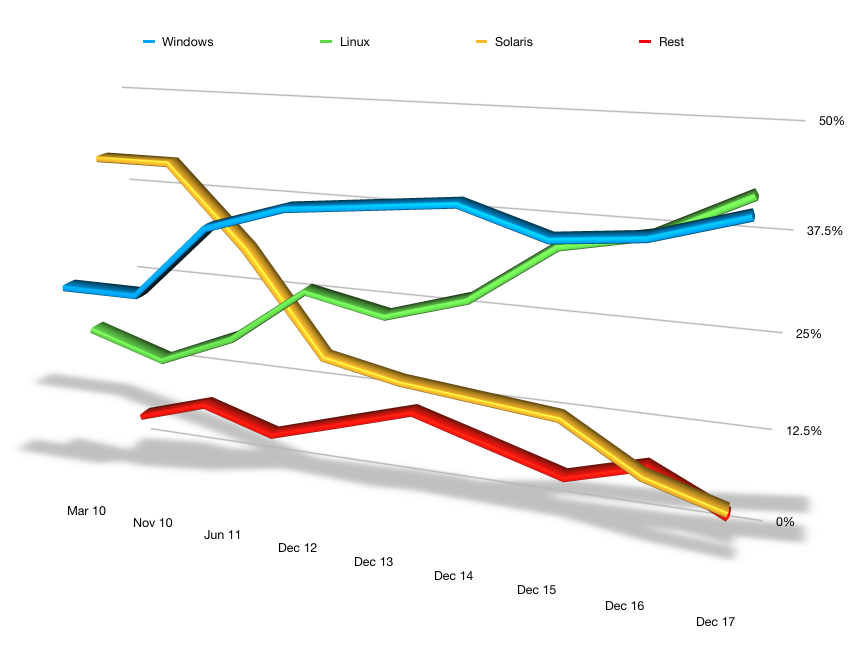
What client/storage node operating systems are you using?
While NetWorker v9.x onwards can only be run on Windows or Linux, there’s still a larger number of storage node platforms supported, and of course, a very large number of client operating system types also supported (or in some cases, still being used, whether specific OS versions are still supported by their primary vendor).
- Linux (RPM based): 69
- Linux (non-RPM based): 23
- Linux (z/OS): 8
- NT4: 2
- Windows 2000: 10
- Windows Desktops: 10
- Windows 2003: 27
- Windows 2008/R2: 60
- Windows 2012/R2: 64
- Windows 2016: 40
- Tru64: 2
- Mac OS X: 6
- AIX: 17
- HPUX: 9
- Solaris: 30
- OpenVMS: 6
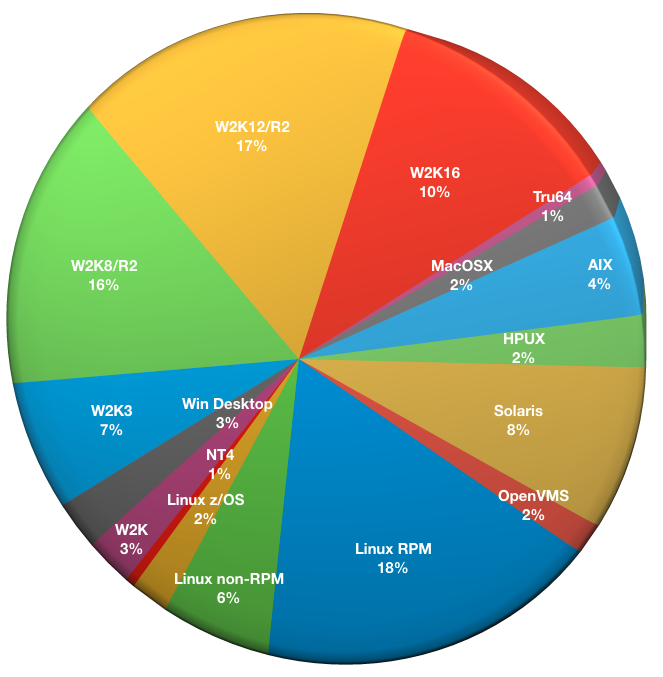
We still see a wide variety of operating system types in use within NetWorker environments. (Perhaps disappointingly, we also continue to see a large number of operating systems that are no longer supported by their primary vendor in use – surely a matter for risk officers within organisations to be evaluating more deeply.)
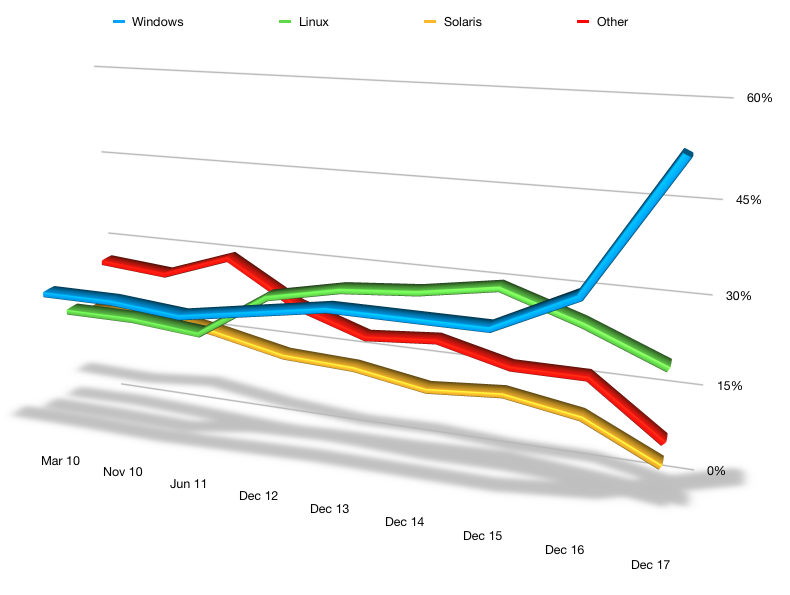
Interestingly, while Linux pipped Windows for the lead for NetWorker server operating system types for the second year running, it has dropped in client/storage node use in this survey, with Windows operating systems spiking considerably:
Are you using backup to disk in your environment?
This question covers whether or not backup to disk (of any kind) is used within an environment. Since more than one type of backup to disk can be used, this was a multiple choice question. Responses were as follows:
- No: 4
- VTL with Deduplication: 8
- VTL with Plain Storage: 2
- Advanced File to Deduplication Storage: 15
- Advanced File to Plain Storage: 13
- Data Domain Boost: 62
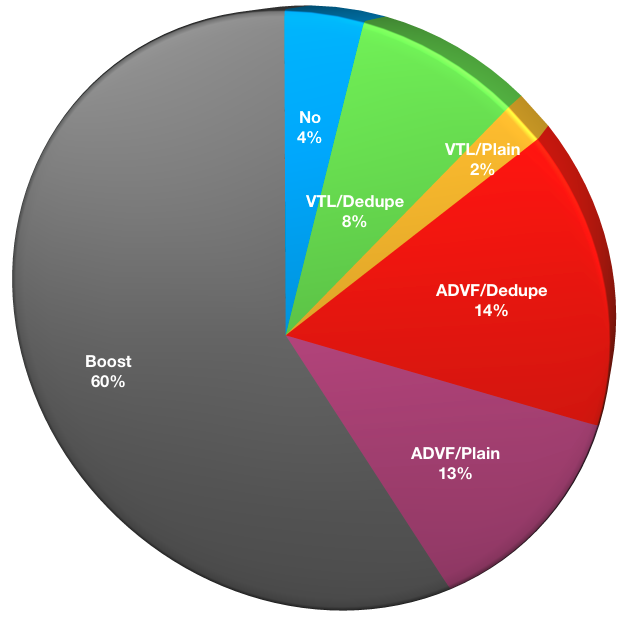
It remains the exception, rather than the rule, to find environments that are not using backup to disk in some form within their environments. NetWorker customers have voted with their feet and are achieving highly optimised backup to disk solutions by combining with Data Domain Boost.
We are also understandably seeing the decline of VTL as a backup storage option – VTL overall offers little enhancement over tape other than a lack of shoe-shining, while still retaining most of the downsides of tape – concurrent usage limits (in fact, deduplicating tape often requires write-parallelism of 1), lack of random IO, etc. As a technology, it entirely represents an evolutionary dead-end. (Aside: there is perhaps nothing more silly in terms of data protection storage than public-cloud VTL.)
Are you using deduplication in your environment?
It’s increasingly uncommon to find a NetWorker environment where deduplication is not being used. Deduplication introduces new levels of efficiency in storage for backup environments, making disk based backup systems more economical, and allowing the operational benefits of moving away from tape to be realised.
- No deduplication: 9
- Source deduplication: 3
- Target deduplication only
- Source and target deduplication: 45
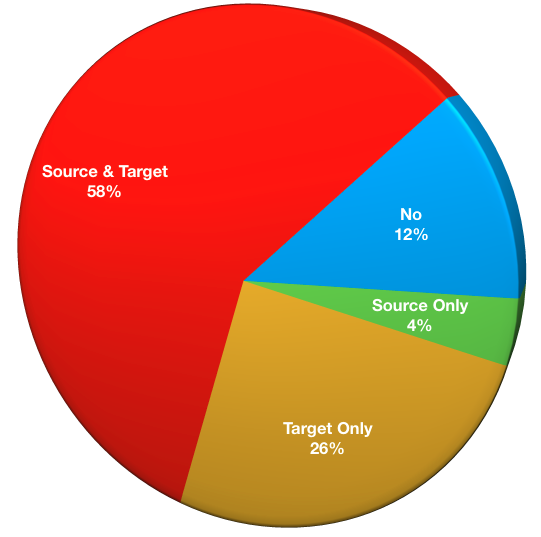
Overall the ratio of deployments not making use of deduplication vs those making use of deduplication has stabilised over the 2016 and 2017 surveys; for 2016 it was 13%, for 2017 it is 12%. This may be representative of the 10% or so of the market that is on the slowest side of the product adoption bell-curve, or for very small datasets.
What type of deduplication are you using in your environment?
Since there is the potential for more than one form of deduplication to be used (for example, Data Domain systems can support simultaneous access via all its available protocols), this was multiple-choice, and yielded responses as follows:
- No deduplication: 9
- Non-EMC deduplication: 8
- Boost protocol: 65
- CIFS/NFS (as in, accessing deduplication over CIFS or NFS): 16
- Avamar: 14
- VTL: 15
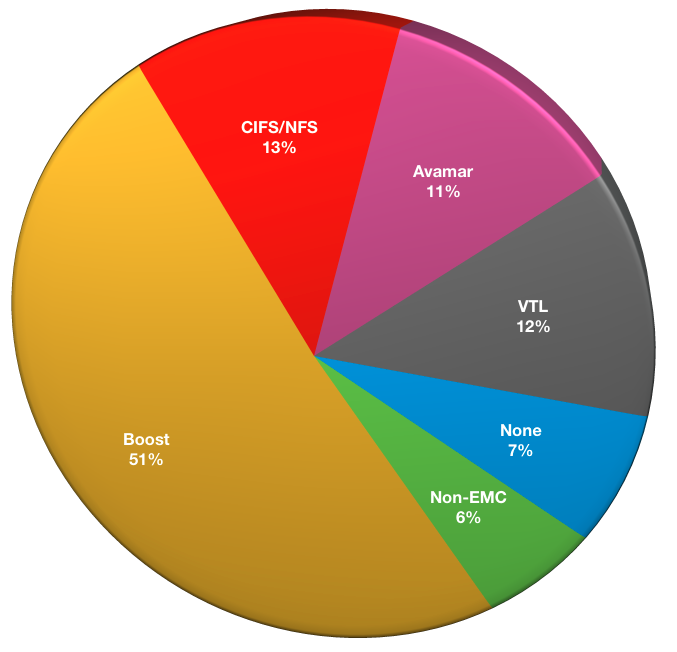
Non-EMC deduplication continues to remain quite low (2014: 8%, 2015: 7%, 2016: 3%, 2017: 6%). The overall operational advantages provided by Data Domain Boost based protocols allows for significant synergies between the data protection software and the storage platform. It is expected that Avamar levels remain higher due to people understanding the background protocol used in the VMware protection layer offered by NetWorker.
What is virtualised within your environment?
The number of environments with no virtualised systems within their environment continues to run quite low, again under 5% in the 2017 survey. This is a multiple choice question since the focus covers: Servers, Storage Nodes, and Clients.
- Nothing virtualised: 4
- Some clients: 52
- All clients: 15
- Some storage nodes: 18
- All storage nodes: 7
- Some NetWorker servers: 19
- All NetWorker servers: 25
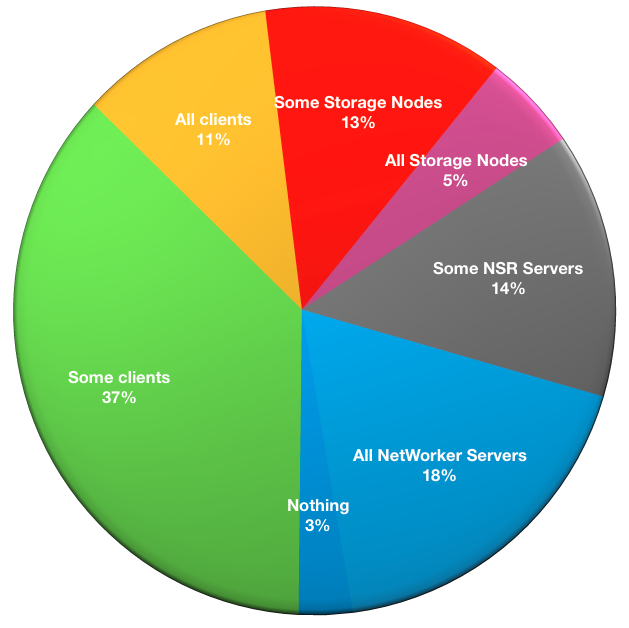
We see in the results a continuing high level of virtualisation.
What hypervisors are in use by your business?
This question was introduced for the first time in the 2017 survey, and is designed to help understand what hypervisors are in use in businesses that are using NetWorker. Given it is increasingly common to see more than one hypervisor in use, this was a multiple choice question. (The one hypervisor available for selection in the multiple-choice selection that received no votes was Parallels, and this has been excluded from the results.)
- VMware: 70
- Hyper-V: 21
- Oracle: 5
- Acropolis: 1
- Xen: 3
- HP Unix based virtualisation: 1
- AIX based virtualisation: 10
- Solaris based virtualisation: 12
- Other hypervisor: 2
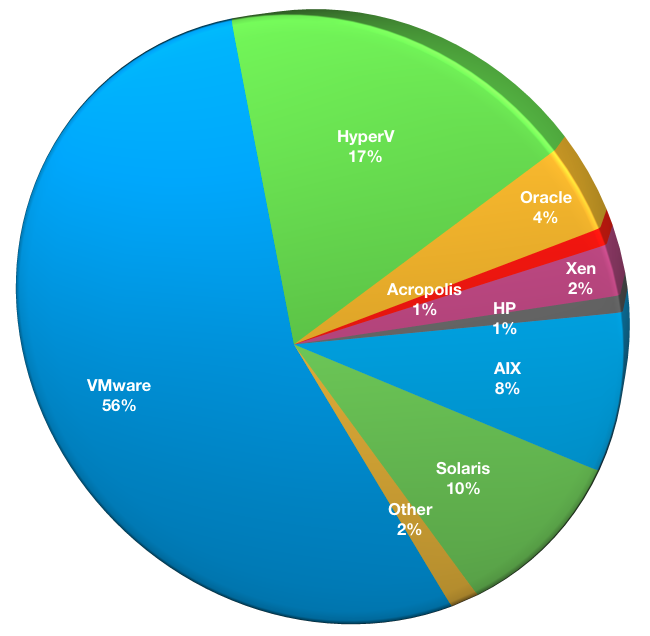
Understandably, VMware as the market leader in hypervisor technology represented more than 50% of the hypervisor selections in respondents. Hyper-V, bundled for free with particular releases of Windows server, occupies 17% of respondent choices. The Unix based options (particularly Solaris and AIX) are well represented, given it is increasingly the default mechanism for resource allocation on legacy Unix systems.
How are you backing up virtual machines?
This is a multiple-choice question, since different technologies can be deployed depending on the version of hypervisor or NetWorker, and the recoverability requirements.
- In-Guest: 47
- VCB: 1
- VADP: 10
- VBA: 20
- vProxy: 25
- VSS: 6
- 3rd Party: 5
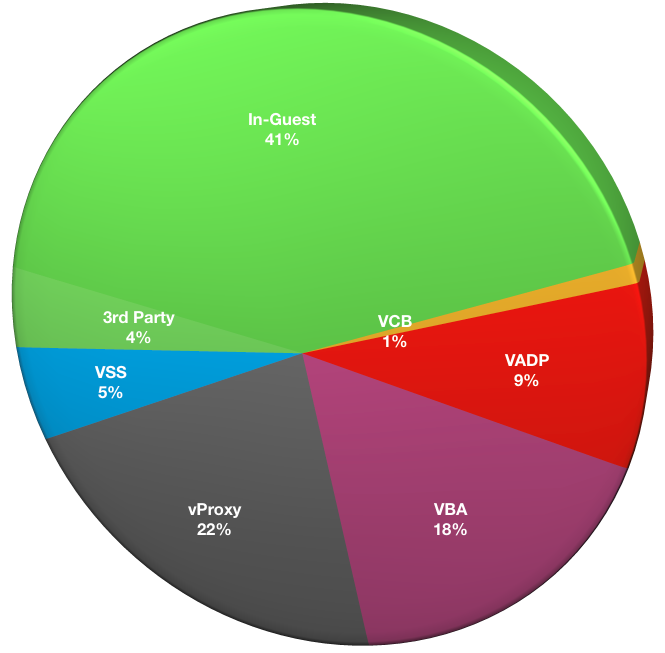
vProxy use is already at 22%, a good indication of the popularity of the new functionality introduced into NetWorker 9.1. Universally, NetWorker users I’ve spoken to have been blown away by the efficiency of the NetWorker Virtual Proxy (NVP/vProxy) compared to prior VMware backup methodologies, and we are seeing rapid uptake by businesses moving to 9.1+ releases. (If you’re still unsure about vProxy, be sure to reach out to your Dell EMC systems engineering team for a demo – you’ll be quickly convinced.)
Are you cloning your backups?
Perhaps the simplest mistake a business can make when it comes to data protection is to allow the backup environment to become a single point of failure. To avoid this, backups should always be cloned. Reassuringly, respondents largely understand this:
- Clone all backups: 28
- Clone production backups: 12
- Clone selective backups: 28
- Don’t clone – not interested: 4
- Don’t clone – no time: 1
- Don’t clone – no budget: 4
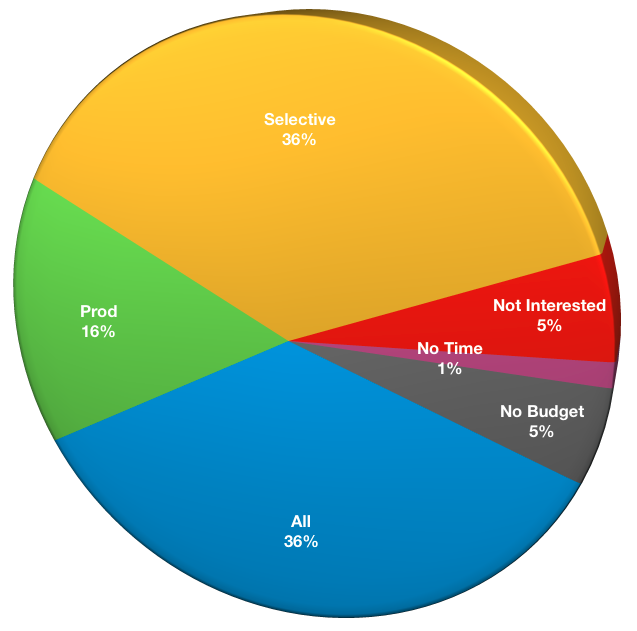
The number of respondents that don’t perform any cloning continues to drop, down another 1.6% compared to the 2016 survey, with 88% of respondents indicating they perform some level of cloning within their environment.
Are you using tape within your environment?
The highest percentage of respondents to any individual option (even allowing that people could select more than one option) was “No”. Following that, tape saw more use as a cloning target than an actual backup target. Responses were as follows:
- No tape: 24
- Selectively used for backup: 10 (Selective B)
- Used for daily backups: 13 (Daily B)
- Used for weekly backups: 9 (Weekly B)
- Used for monthly or longer retention backups: 14 (Monthly+ B)
- Selectively used for cloning: 16 (Selective C)
- Used for daily cloning: 14 (Daily C)
- Used for weekly cloning: 10 (Weekly C)
- Used for monthly or longer retention clones: 21 (Monthly+ C)
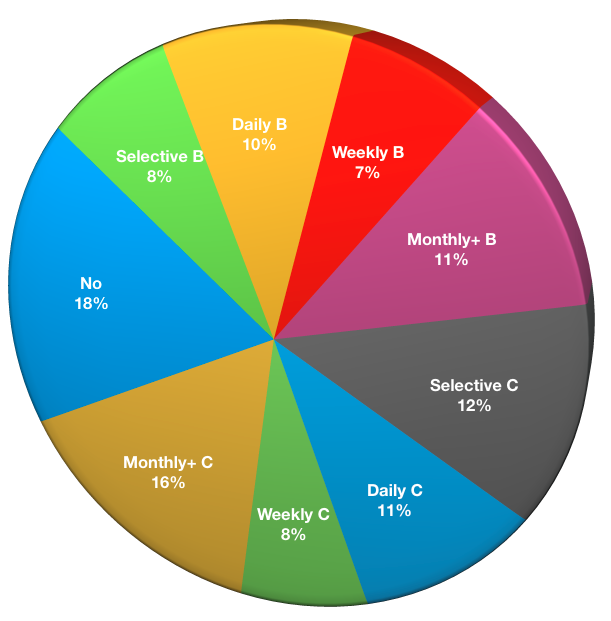
The demise of tape is a long and slow process. It will be interesting to note the impact of legislation such as the EU’s GDPR on the ongoing use of tape within backup systems, since tape’s access and usage profile is completely at odds to how GDPR requires businesses to react to customer requests.
What is your longest retention time?
Answers to this question were as follows:
- Less than (or equal to) 31 days: 5
- 1+ to 3 Months: 6
- 3+ to 6 Months: 4
- 6+ to 12 Months: 11
- 1+ to 3 Years: 8
- 3+ to 7 Years: 16
- 7+ to 15 Years: 22
- 15+ Years: 5
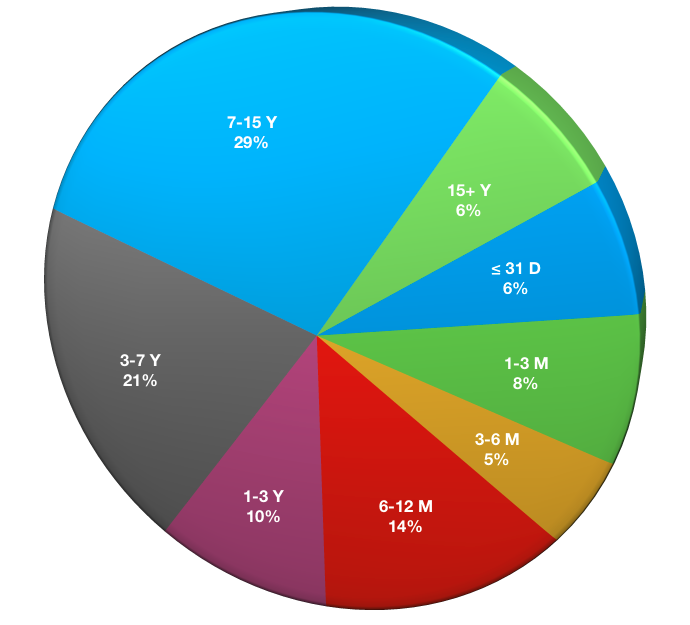
Longer retention times (1 year or longer) are more the rule than the exception in most backup environments. We tend to see very short retention times only in environments where:
- Extensive archive operations are performed (i.e., full data management)
- Backup is being provided as a limited service to subscribers or consumers
- A no-delete policy is followed
- Insufficient review of the legal implications of failure to recover has been conducted.
How long has NetWorker been in use at your business?
Backup software tends to be sticky within many environments, especially when it is exceptionally powerful, extensible and reliable such as with NetWorker.
- Less than (or equal to) 1 year: 2
- 1+-2 Years: 2
- 2+-5 Years: 17
- 5+-10 Years: 21
- 10+-15 Years: 12
- 15+ Years: 23
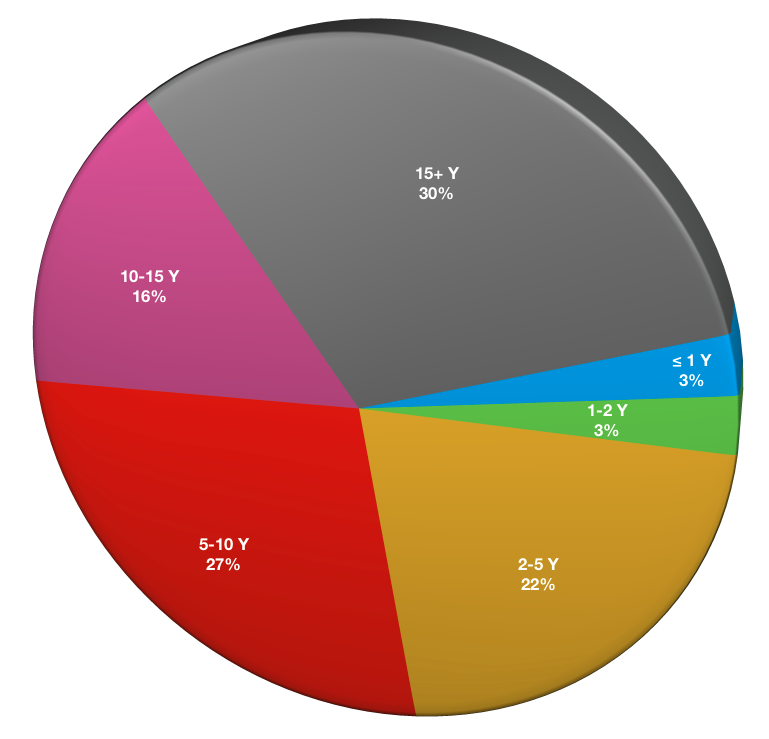
73% of respondents businesses have had NetWorker installed for 5+ years.
Has your business been hit by ransomware?
Ransomware remains a hot topic in IT, simply because of its prevalence. Cyber-criminals cost businesses billions annually, and “cyber-insurance” is now becoming increasingly common. Ironically, cyber-insurance would not be required at all if businesses follow appropriate data protection practices (off-platform copies, security hardening of data protection environments, and where required, airgapped or Isolated Recovery Site environments).
Responses to this question were as follows:
- No: 36
- Don’t know: 10
- Prefer not to say: 7
- Yes: 24
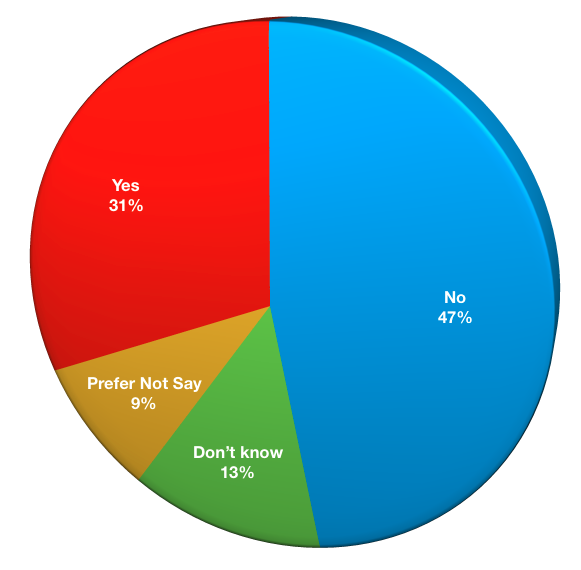
This question was first introduced in the 2016 survey, where 48% of respondents indicated they’d not been hit by Ransomware, and 31% indicated they had been hit. In this, we see a slight increase in the “don’t know” category, with “prefer not to say” continuing to hover just below 10%.
(Anecdotally, when I speak to businesses about data protection implications for ransomware, it is common for people to initially say their business has not had an attack, but as the discussion progresses and it becomes apparent that ransomware is a common thread for many businesses, many explain that such attacks have, in fact taken place. We can therefore assume that “prefer not to say” will more often than not mean “yes”, as opposed to “no”.)
What is the status of backup encryption within your environment?
Backup security is slowly gaining attention within jurisdictions world-wide, with a slowly increasing focus as well to breach disclosure legislation in addition to regulated levels of security. This has not yet fully penetrated to the point where more than 50% of respondents highlight a need for, or an implementation of encryption, but such a time will undoubtedly come.
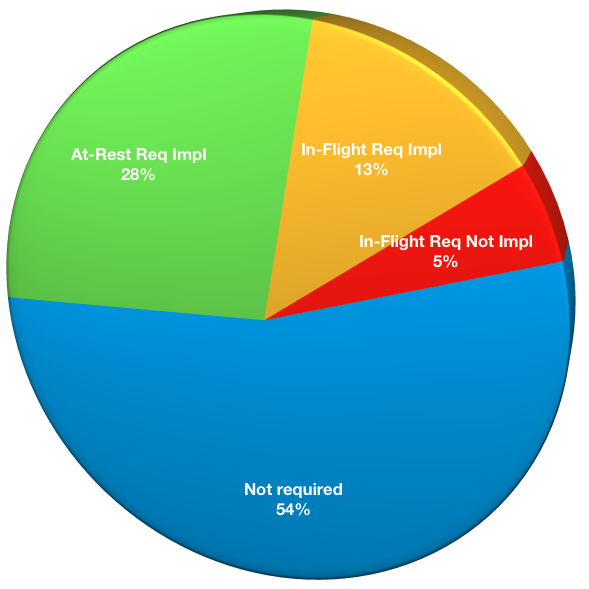
- Encryption not required: 43
- At-rest encryption required, and implemented: 22
- At-rest encryption required, not implemented: 0
- In-flight encryption required, and implemented: 10
- In-flight encryption required, not implemented: 4
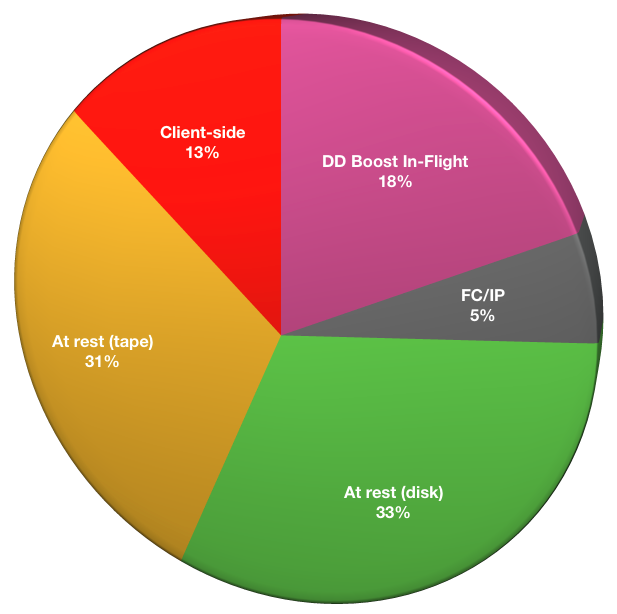
For those who are using encryption, it is always useful to know how encryption is actually being achieved. Respondents were as follows:
- At-rest on disk: 18
- At-rest on tape: 17
- Client-side (software): 7
- Boost in-flight: 10
- Fibre-Channel/IP Router encryption: 3
Do you have dedicated backup administrators?
There was once a time I’d have said every business must have dedicated backup administrators, unless it’s got an IT department fewer than say, 10-20 people.
- Yes: 43
- No: 34
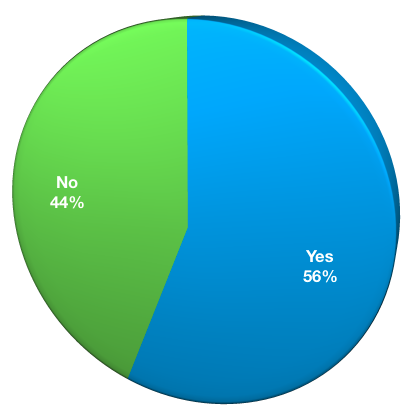
The backup administrator is a role that’s going to change over time. As I discuss in my book, we are at a point in time where cloud approaches to infrastructure (be they on-premises or via public clouds), the approaching “software defined datacentre”, and hyperconverged are driving a new form of administrator: a full stack administrator. Over time, dedicated backup administrators will more demonstrate a “legacy” approach to infrastructure, where each role comes from a very specific silo within the IT organisation. Furthermore, we will see the rise of the data protection advisor, or data protection architect – increased automation functionality within data protection will free up backup administrators in particular from tedious daily duties and allow them to fulfil a higher level design and monitoring role.
Do you have public cloud workloads?
Public cloud is going to continue to be a focus for business for some time to come. (For all the benefit businesses can realise from making use of particular cloud principles (e.g., elasticity and on-demand consumption/measurement), there are two quick asides I’d like to make. First – I find it humorous to hear people talk about a fear of “vendor lock-in” relating to on-premises infrastructure while embracing public cloud, which can represent extreme levels of lock-in; second – true return on investment (ROI) calculations for public cloud workloads should be performed over the expected lifespan of the data or business function, rather than a short-term, maximum 1-year approach favoured by public cloud providers.)
Respondents answered as following for this question:
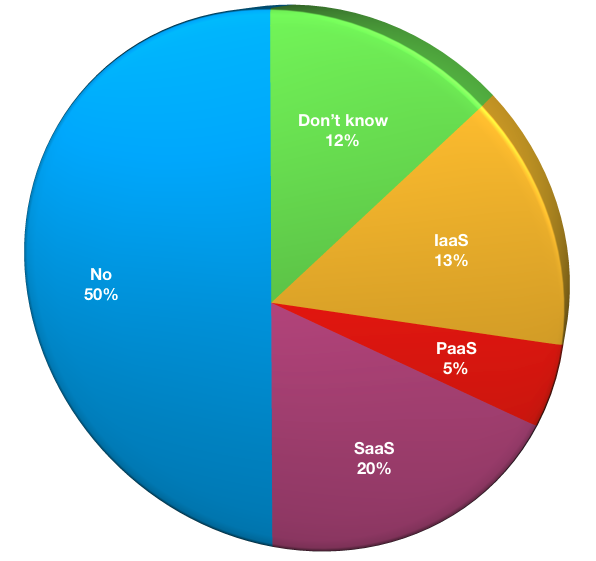
- No public cloud workloads: 41
- Don’t know if there are public cloud workloads: 10
- IaaS workloads: 11
- PaaS workloads: 4
- SaaS workloads: 16
For those respondents who had public cloud workloads, the follow-up question of course was: how are you protecting them?
- Don’t know: 13
- Rely on public cloud vendor: 13
- SaaS backup: 3
- Backup to DC: 3
- Backup in Cloud: 7
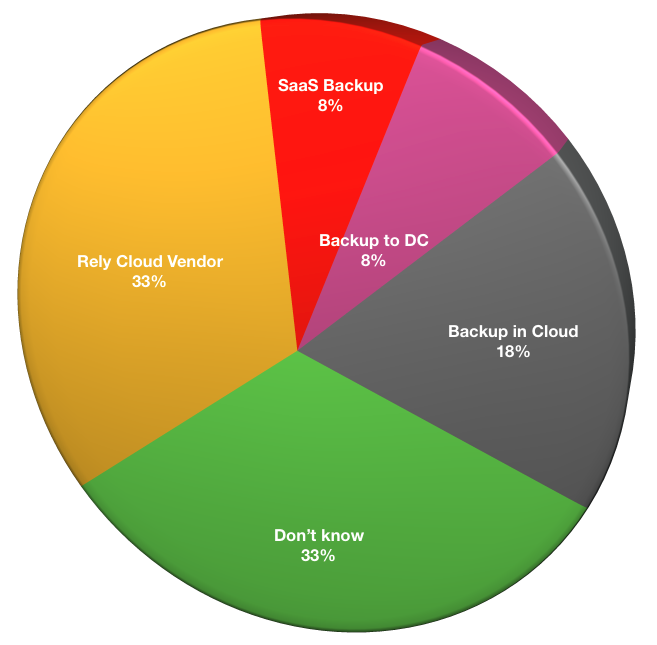
While the respondent numbers are low on this question (due to the lower number of respondents using the cloud), the key point I’ll note is that too many people who are responding on a backup survey do not know how workloads are protected in public cloud, which speaks to a risk within the business.
Are you using, or planning to use, Cloud Object storage for backup?
It is still relatively early days when it comes to the use of cloud object storage for backup (either direct, or for long term retention). Note that Cloud Object does not necessarily refer to public cloud – Elastic Cloud Storage (ECS) for instance is a highly popular option for Dell EMC customers who are moving to object storage with backup. Public Cloud use will be dependent on a wide variety of factors, including link speed, link cost, whether or not a full ROI has been performed on data lifecycle (for example: unless you have a very small amount of data, keeping LTR data in public cloud, vs on-premises cloud, is costly).
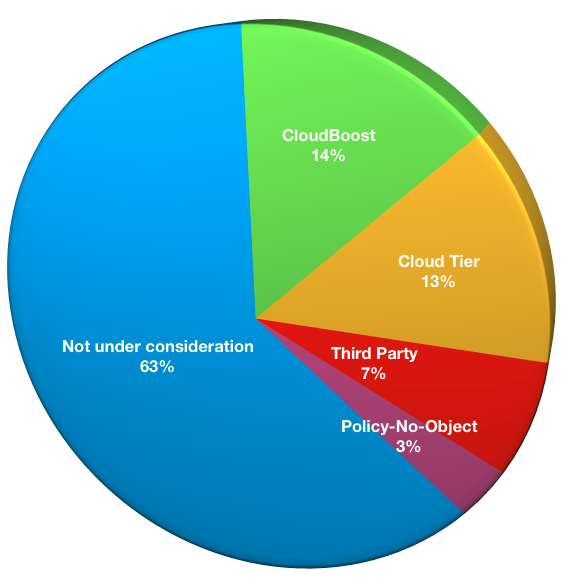
Responses to this question were:
- Not under consideration: 55
- Active policy to not use object storage: 3
- CloudBoost: 12
- Cloud Tier: 11
- Third Party Method: 6
(Since a number of cloud object options can be used, this was a multiple choice question.)
What modules are you using?
This question was multiple-choice, allowing respondents to indicate what modules, or plugins, they are using with NetWorker beyond virtualisation support and filesystem backup. Note that in the abbreviated module details below, “L-” refers to “Legacy” – e.g., “L-Oracle” refers to the legacy “NMO” module that was amalgamated into the NetWorker Module for Databases and Applications (NMDA).
- NMM: 51
- NMDA: 38
- NDMP: 34
- NAS Snap: 1
- Boost RMAN: 9
- Boost for Databases: 7
- Boost for Exchange: 11
- Boost for SQL: 16
- BoostFS: 4
- L-Oracle: 19
- L-Exchange: 15
- L-SQL: 24
- L-Sybase: 3
- L-SAP on Oracle: 13
- L-DB2: 4
- L-Informix: 1
- PowerSnap: 1
- Meditech: 1
- MySQL: 1
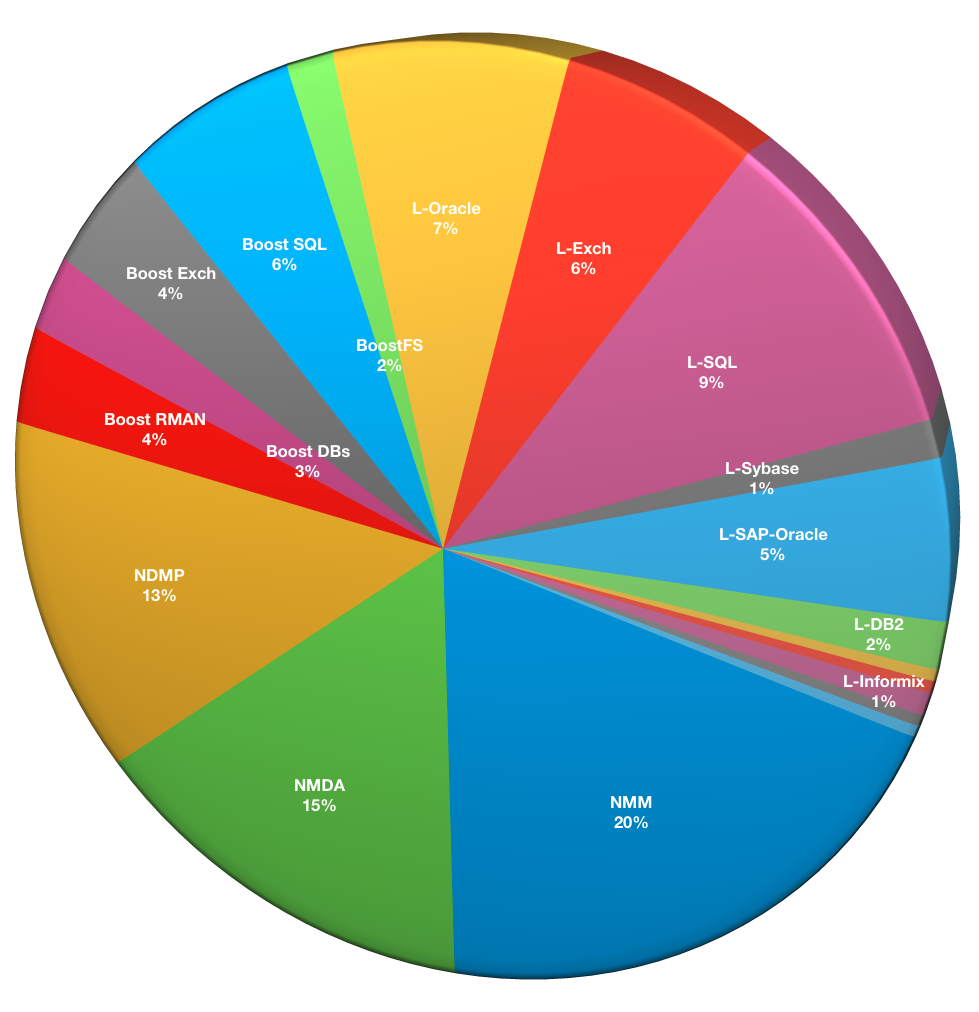
This remains a wide spread selection of usage profiles with NetWorker, with NMM, NMDA and NDMP retaining the “lion’s share” of special usage profiles.
Summary
It’s interesting to note there are several areas where we’re seeing relative stabilisation in results – such as the percentage of environments not using virtualisation, and the percentage of environments not making use of backup to disk or deduplication. In this we’re seeing (from a classic “bell curve” perspective), the ‘laggard’ percentage established. These will undoubtedly be the environments where infrastructure spend is low, or every last drop of value is wrung from infrastructure between refresh cycles.
NetWorker 9 adoption has, as we would expect, gained traction as more features and functionality has been introduced (particularly vProxy), and older versions have approached or exceeded their end-of-support date.
Hi Preston,
thank you very much for sharing your report. Well done. I’ll really appreciate it.
I just cannot any download link – did you provide one at all?
Hi Carsten,
Thanks for the feedback. For this report there’s no download link – due to time constraints I did it as a blog post to ensure it got out and there were no further delays.
I’ll be curious to see whether this is seen as a better, worse, or neutral option.
Cheers,
Preston.