OK, let’s look at common data protection challenges through the eyes of memes again!

I’m a big fan of backup monitoring. When I was a backup administrator, I’d spent anywhere up to the first hour of each day reviewing all the NetWorker savegroup completion reports that would come in overnight and actioning them. Ah, those were the days! But, those days are gone – you just don’t have the time to sit and read an email for each backup group or policy that’s run each morning. The business expects you to do more, with less – and that means more work with less time. So that means for many of us, our unread badges look something like this:

Not me. I get the screaming heebie-jeebies if I see lots of unread badges somewhere. I don’t subscribe to Inbox Zero, but I’m just not a fan of knowing there are all sorts of emails and messages I need to get to.
If you’re a backup administrator (or increasingly, an infrastructure administrator), you should be able to just glance at a data protection dashboard at the start of the day and see whether there’s anything you need to dig into. In my opinion, that’s probably the best thing Data Protection Central gives you is this:
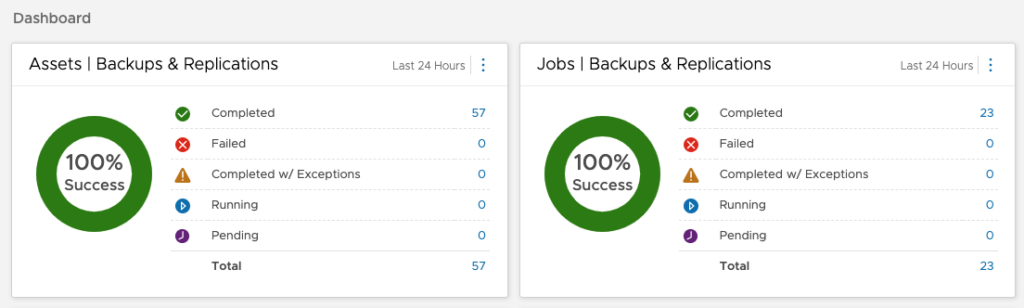
Sure, it’s not always going to be 100% successful every day. I won’t pretend otherwise: backup, and data protection more broadly has too many systems involved to get 100% success 100% of the time. But you don’t need to read (or receive) all those individual backup notifications if you can look at a single dashboard and see whether things have been working – especially if that allows you to drill in on any failures (as DPC does).

My first encounter with auditors involved having to refute a scathing report where our team was judged to be willfully apathetic towards security because the password for every account on our systems was ‘*’. Reality: that’s what was in /etc/passwd, because we were using /etc/shadow. We really did have good passwords.
It seems everyone has at least one bad story when it comes to auditors. That’s not to say that you can’t have good stories when it comes to auditors. After all, most of the time they’re just doing their job – their goal is to help you prove to the business that everything is A-OK.
If the business you work for has to be periodically audited for compliance relating to data protection KPIs and practices, your most invaluable tool is going to be Data Protection Advisor. Configured correctly, it’s going to give you a wealth of data, including:
- Adherence to KPIs, including:
- Backup success ratios
- Replication success ratios
- Recovery success ratios
- Backup and replication timeframes
- Security access monitoring/reporting
- 3-Strike reports (DPC will give you that, too)
- Report-cards
- and so much more
Even things as straight-forward as the backup report card can make your life easier when it comes to successfully completing audits. What’s more, those sorts of reports are going to make your day-to-day job so damn easy, too:
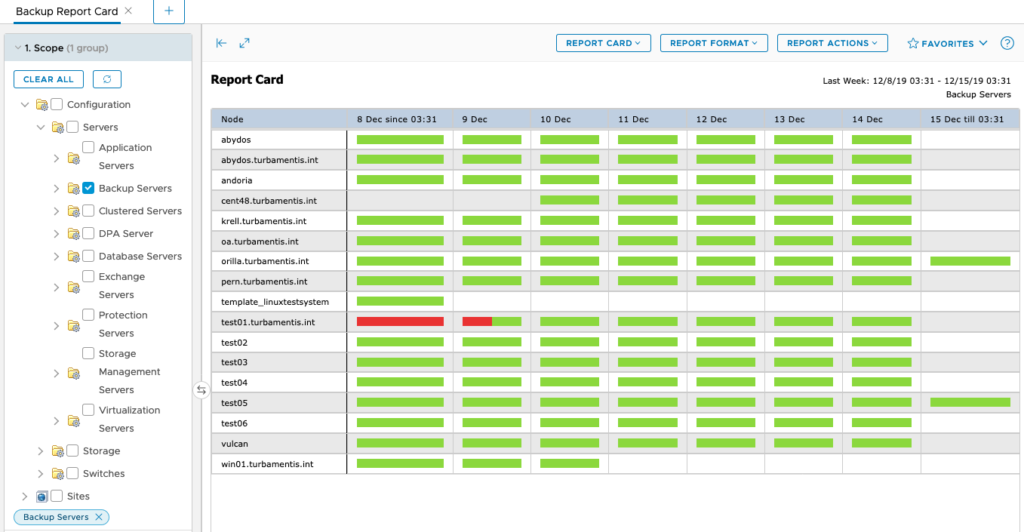
Imagine being challenged by an auditor about your success ratios for backup and recovery and producing, within seconds, a report showing your results for the past month?
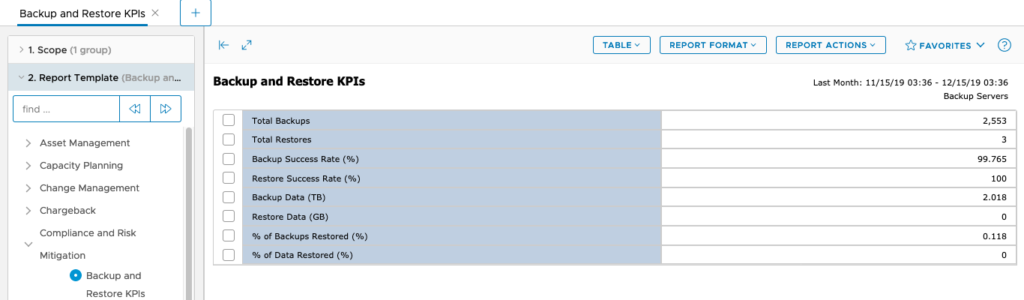

Source side deduplication – true, source-side deduplication, is crazy fast to watch. It’s common to see even within large organisations that 99.9% or more backups, done as a full backup every day, complete in less than 30 minutes.
Can you imagine that? If you’re still stuck in a three-tier architecture going to tape, it’s a big jump. Sure, daily incrementals might not take too much time, but what about daily fulls? I remember when I was a backup administrator shuddering any time someone asked me if we could do a full backup of such-and-such a system each day.
There are times when you need to do target-based deduplication. I get that. But those times should be few and far between, and should be the exception rather than the rule? Why would you waste your network bandwidth and backup window sending 100% of your data over the LAN only to throw away 95% of it? Why not throw away 95%-99% of it before it even leaves the client? That’s the joy of source-based deduplication.

When I used to do backup implementation and support services, I don’t know how many times I’d have that sort of bone-chilling conversation with a customer where I’d have to tell them that they couldn’t recover some filesystem because they’d configured NetWorker to only backup specific filesystems, and never included that particular path.
You see, NetWorker, like other enterprise backup products, has special “auto-selection” options that tell it: “back up everything automatically mounted on this client”. NetWorker literally calls it the “All” saveset. For Avamar, it’s the default of having “All Local x filesystems” as the dataset selection. I call these products Exclusive selection products because if there’s anything you don’t want to be protected, you have to explicitly exclude it. (The opposite, Inclusive selection products, require you to explicitly include everything you want to be protected.)
The lesson here is simple: if your data protection product is zealous about making sure your data is protected, be very, very careful about deciding to force it to behave differently. It may seem like you’re getting some cunning space savings in the short term, but in the long term you, or someone who follows after you in your role, may have a very uncomfortable discussion ahead.
