It’s fair to say that a significant number of my customer conversations this year have been centred around cyber resiliency. This is not that surprising — it’s a huge topic across practically every industry vertical as cyber attackers are getting bolder and more sophisticated. The size of the cyber-crime industry is truly breathtaking and only continues to grow.
Cybersecurity Ventures expects global cybercrime costs to grow by 15 percent per year over the next five years, reaching $10.5 trillion USD annually by 2025, up from $3 trillion USD in 2015. This represents the greatest transfer of economic wealth in history, risks the incentives for innovation and investment, is exponentially larger than the damage inflicted from natural disasters in a year, and will be more profitable than the global trade of all major illegal drugs combined.
“Cybercrime To Cost The World $10.5 Trillion Annually By 2025“, Steve Morgan, Cybersecurity Ventures, 13 November 2020.
Five years ago, when I started having cyber resiliency conversations with customers, it was a relatively rare discussion and mostly focused on ransomware/cryptolocker scenarios. That’s certainly not the case any longer.
Do I need a Cyber Resiliency Strategy?
Let’s start with the easy question. If you’re reading this and wondering whether you need a cyber resilience strategy, I’ll answer with the following diagram:
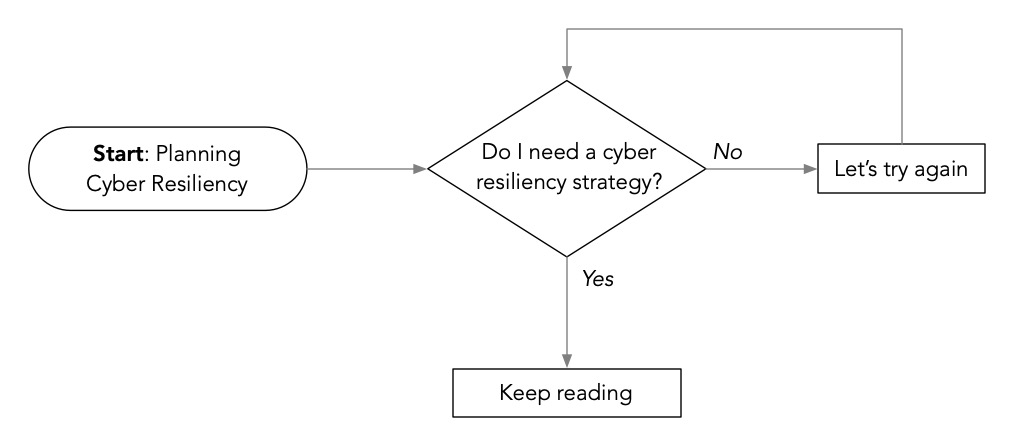
Given the way cyber threats are evolving, the only reason to not be actively developing a cyber resiliency strategy is if you already have one. And even then, it should be a living strategy that’s regularly re-evaluated.
What Data do I need to Focus on for Cyber Resiliency?
Cyber resiliency isn’t something you get from standard disaster recovery processes. Instead, to get into a cyber-resilient posture, you need to focus on providing additional protection for three critical slices of data for your business.
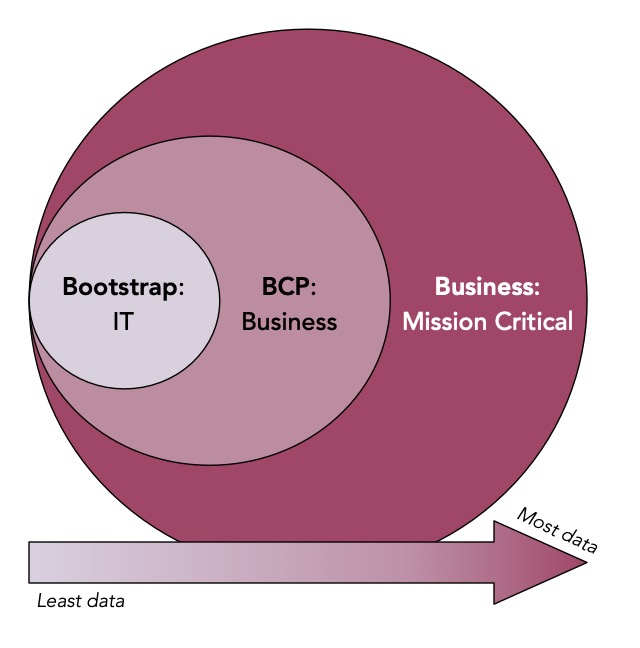
I’ve drawn these as layers for one critical reason: when businesses start considering cyber resiliency solutions, they can readily suffer from analysis paralysis in the mistaken view that the solution deployed on day one needs to ‘boil the ocean’.
While ideally it might be nice to deliver a cyber resiliency solution to the business that does everything on day one, the reality is that as you step through each of those layers, the amount of data required, and the amount of analysis required to assemble that data increases – usually on a steepening curve. I wouldn’t call it exponential, but it’s certainly non-linear.
As to what those data slices are, here’s a quick perspective:
- Bootstrap IT: What essential data elements do you need to get the core IT services up and running? Effectively, you’re looking at the minimum viable components that allow you to conduct service restoration. These will be things like DNS, authentication, password databases, etc.
- Business Continuity Pieces: You can think of this as ‘business continuity process lite’. What are the fundamental pieces of business data you need to help keep the lights on? A lot of this will be related to payroll, HR and planning/processes around disaster scenarios.
- Mission Critical Business Data: What’s the data (and systems supporting that data) required to keep the functional lights on for the business? How do you ship product, achieve basic customer service, billing, meet regulatory requirements, etc.?
There’s work involved in each one of these areas! Bootstrapping the IT environment, while the simplest of the three, is getting increasingly complex due to system dependencies, and includes the sorts of things that are readily forgotten (e.g., DNS, network and fibre configuration, firewall configs, etc.). Yet, this should be easier and simpler to deal with than the other two, and so it’s always a good place to start.
How Do I Determine that Data?
As I mentioned, determining each of those data slices requires an increasing amount of effort, which is why you start at the smallest and work your way out.
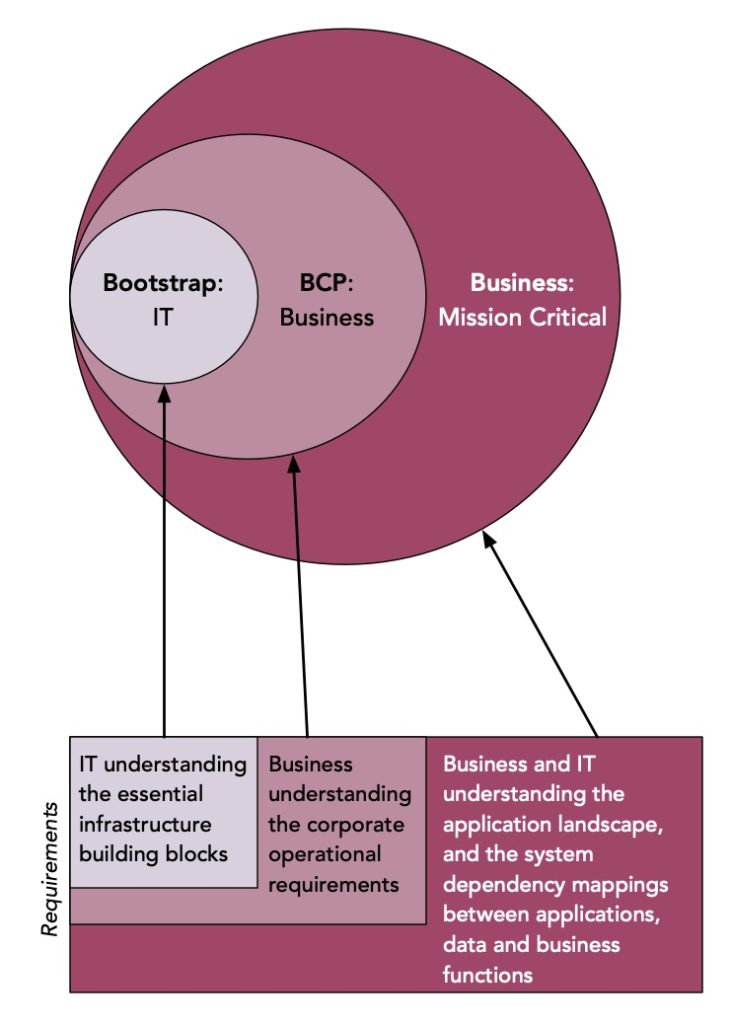
Getting the IT bootstrap information right comes down to the IT department understanding the essential building blocks for business infrastructure. In the simplest scenario, that might come down to asking each team within IT to nominate their essential data. But, a multi-team panel, or even an external agency should ‘ride shotgun’ to provide additional validation that nothing has been forgotten. (I always remember the first actual disaster recovery exercise I was involved in as a Unix system administrator. We thought we’d accounted for everything, and the exercise failed within mere moments of starting when we realised we hadn’t thought of DNS.)
If you’ve read my books, you’ll know that I’m a big fan of system dependency maps. Regardless of whether you follow a manual or automated process to build them, they allow you to see the interdependencies between data/systems at an IT level and business functions. They help you understand what’s needed at the back-end to provide a particular business service – e.g., online shopping, order fulfilment, etc. While the users and customers of the business typically only see those business functions, they can be the tip of the iceberg in what’s needed. So it’s all well and good to say “our ERP system is mission-critical”, but what else is involved in actually allowing the ERP to run? That’s why working out the mission-critical data to protect under a cyber-resiliency strategy is the most complex. Ideally, you’ll need all the following:
- Application discovery
- System dependencies
- System criticalities
- Regulatory requirements
Especially if you have to start from scratch (e.g., if you’re moving from a relaxed to a formal governance model), those details could take you weeks or months of planning – so why not start small with the IT and business bootstrap details while you’re working towards it?
Final Thoughts
There are two fundamental mistakes commonly made when it comes to cyber resilience. These are:
- Thinking you don’t need it, and
- Thinking you have to boil the ocean.
Neither is true. And even within a cyber resilience strategy, there are different layers or levels of protection you might want to plan for, depending on the risks and budgetary appetite your business faces. These can go up to deploying a complete cyber recovery solution. However, there’s more in a cyber recovery solution than just hardware and software! It’s people, processes, and a consultative discovery approach that runs before, during and after software and hardware is dropped into a datacentre.
That cyber recovery solution doesn’t have to be huge – it should be a focused endeavour. And just like the planning and analysis you do for cyber resilience, a cyber recovery solution can start small and build up over time to encompass those various data slices.
