Government regulators in most countries can be slow to get moving, but when they do, they can cause significant changes for businesses. While many businesses had internal policies prohibiting the behaviour, you may recall last year that a stark warning came out about paying ransomware demands:
Companies paying ransom when attacked by ransomware in an effort to retrieve their data has always been controversial because it encourages future attacks. Now, doing so may also be illegal.
The U.S. Department of Treasury today warned that paying ransomware demands may be illegal and that companies that do so could be prosecuted.
Treasury Department: Paying ransomware demands could be illegal, Duncan Riley, Silicon Angle, 1 October 2020.
An endemic problem in business at the moment is the perception that ransomware is merely a security issue. There’s an element of security to it, but it’s wrong to think that you can somehow deploy security so impenetrable and fool-proof that Ransomware can’t get you. Despite the warnings to the contrary, many businesses have found themselves paying ransom demands in return for their data, having failed to contemplate the backup and recovery aspect of the issue.
Ransomware, and other forms of cyber-crime, have become such a profitable industry that the cost to the market is increasing beyond billions into trillions. And the attacks are never-ending:
Top US fuel pipeline operator Colonial Pipeline has shut its entire network, the source of nearly half of the US East Coast’s fuel supply, after a cyber attack that involved ransomware.
The incident on Saturday (Friday US time) is one of the most disruptive digital ransom operations ever reported and has drawn attention to how vulnerable US energy infrastructure is to hackers. A prolonged shutdown of the line would cause prices to spike at gasoline pumps ahead of peak summer driving season, a potential blow to US consumers and the economy.
Cyber attack shuts down US fuel pipeline ‘jugular’, Stephanie Kelly and Christopher Bing, The Age, May 9 2021.
Within 24 hours, one potential vector for that attack was rumoured to be DarkSide. If you think Ransomware attacks are coordinated by pimply adolescents with access to some random scripts and hacks they found on the net, think again:
DarkSide is one of a number of increasingly professionalised groups of digital extortionists, with a mailing list, a press centre, a victim hotline and even a supposed code of conduct intended to spin the group as reliable, if ruthless, business partners.
Experts like Div said DarkSide was likely composed of ransomware veterans and that it came out of nowhere in the middle of last year and immediately unleashed a digital crimewave.
DarkSide, ransom group linked to Colonial Pipeline hack, new but not amateur, Raphael Satter, The Age, May 10 2021.
If you’re wondering whether all the talk about ransomware growing to a trillion-dollar industry is hype, you may want to look at the insurance industry. Insurers always know a bad bet when they see one, and so:
In an apparent industry first, the global insurance company AXA said Thursday it will stop writing cyber-insurance policies in France that reimburse customers for extortion payments made to ransomware criminals.
Insurer AXA halts ransomware crime reimbursement in France, Frank Bajak, ABC News, 7 May 2021.
My take on this is that AXA withdrawing from the ransomware insurance business is the pebble that starts the avalanche. For sure, there are caveats to the withdrawal, but where one insurance company treads, others are sure to follow. When there’s a cyberattack every few seconds and businesses taking hits from ransomware every hour, there is no profit for the insurance industry any longer.
Ransomware payments may seem like a quick way of resolving an issue, but they’re like a global version of the prisoner’s dilemma:
The insurance industry has come under considerable criticism for reimbursing ransom payments. Cybersecurity expert Josephine Wolff of Tufts University said it has come to be built into organizations’ risk-management practices “as one of the costs of doing business. And I think that’s really worrisome because that is what fuels the continued ransomware business — people keep paying ransom.”
Ibid.
For too long, businesses have treated ransomware as a security problem. Yet while security professionals are aware of the risk, and seasoned experts have moved on from a purely perimeter-only (“moat”) posture, their focus remains on erecting layered defences and detecting attacks as quickly as possible. That’s only sufficient in a perfect universe — the same universe where zero-day exploits don’t exist and end-users don’t succumb to social engineering attacks.
When I was 17, I had a particularly nasty accident where I cut my foot open at a swimming pool on Xmas day. So swift was the cut that I didn’t actually feel anything, so I casually asked for a couple of band-aids before I was summarily rushed to emergency and received more than 20 stitches and a tetanus booster shot. You may be wondering why I’m introducing such a story here, but the rationale is simple: businesses that turn solely to the security team to address the threat of ransomware are Me, standing beside a pool with a crimson trail spreading out behind, asking, “Can I have a band-aid?”
The evolving nature of ransomware, of course, shows why we equally can’t treat it just as a backup and recovery problem. While strengthening backup and recovery defences to ransomware has been essential, it hasn’t come without consequences as cybercriminals shifted their attack to also one of:
…stealing sensitive data before encrypting networks and threatening to dump it online unless victims paid up. That helped drive ransom payments up nearly threefold to an average of more than $300,000.
Ibid.
Ransomware isn’t even plateauing:
Data from 25,000 small-to-midsize organizations reveals ransomware as the top cyber insurance claim in the first half of 2020, with the average ransomware demand increasing 100% from 2019 through Q1 2020.
Ransomware Was the Top Cyber Insurance Claim in Q1 2020, Filip Truta, Bitdefender Business Insights, September 14 2020.
The criminals working this routine aren’t afraid of taking on big targets, either:
Apple has been targeted in a $50 million ransomware attack following the theft of a trove of engineering and manufacturing schematics of current and future products from Quanta, a Taiwan-based company that manufactures MacBooks and other products for Apple.
Apple targeted in $50 million ransomware attack resulting in unprecedented schematic leaks, Chaim Gartenberg, The Verge, April 21 2021.
On a side-note, this also reflects an ethical challenge to journalism — whether or not they should publish details leaked by cybercriminals. (The website 9to5mac.com clearly had no consideration to the ethical ramifications and published details from the leaks of stolen material. This is significantly different from publishing a whistleblower bringing attention to illegal activities. I vehemently disagree with their approach and won’t link to it.)
In fact, ransomware has now become a perfect example of a business threat that requires a tripartite data protection response:
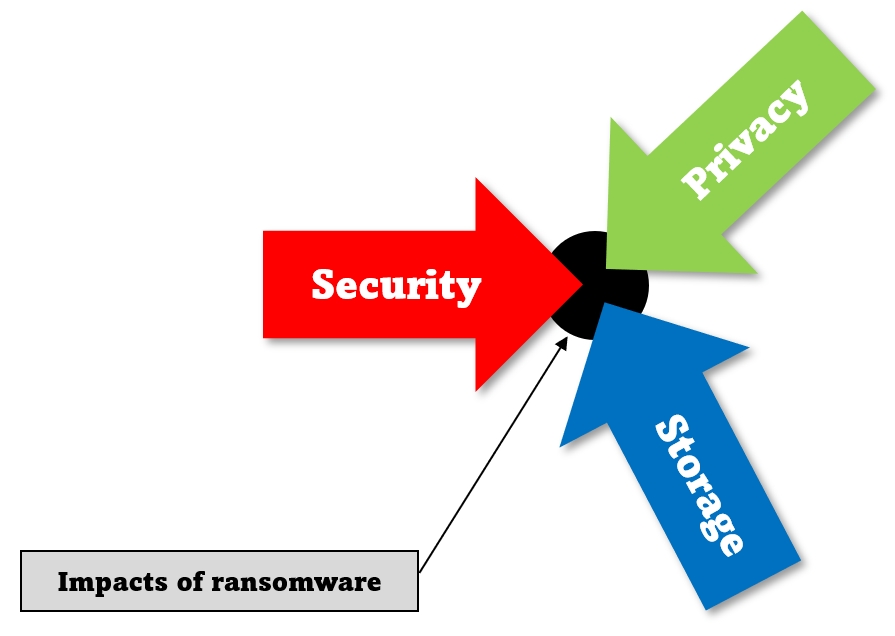
Your business isn’t going to tackle ransomware by assigning it to the practitioners of only one or two of the data protection within the business. It has to be assigned to all three.
It not only has to be assigned to all three — it has to be worked on collaboratively by all three types of practitioners, and they have to start learning from each other. There are no more excuses for backup people to worry about security later, security people to ignore infrastructure, and privacy people to think they don’t even work in IT — that’s merely continuing to walk the current path to increasingly frequent and costly cyber attacks on the business.
No wonder it’s starting to be seen as a bad bet in the insurance industry! If your business policy is to rely on cyber insurance, it’s more than past time to reconsider that approach.

Maybe an overly simplistic worldview (and certainly unpopular opinion as a lot of people have money in the cryptocurrency game), but, if we were to de-anonymize cryptocurrencies, perhaps we would have a lot less ransomware
I completely agree that regulators must turn their attention to cryptocurrency. If a currency is untraceable and anonymous it’s going to be turned towards criminal behaviour. Governments around the world recognise this. Many countries have very strict regulation around cash activities as a means of avoiding labour goods & services taxes — and that’s just at the low-end.
In addition to the environmental impact of cryptocurrency, its popularity among cyber-criminals deserves stronger attention, stronger regulation, and perhaps even dismantling.
Ransomware existed pre-crypto, and the concept is old as time itself. It was just Western Union or just plain old cash.
I think there is a lot of reasons that crypto is bad, and that generally blockchain is a solution looking for a problem no one wants to have.
I remember a time when Viruses were focused on causing destruction, irritation and inconvenience. But Ransomware is here to stay due to the huge swathes of money it makes criminals – with a small group making 250k in 6 days being reported in the paper the other week.
It’s a multi-faceted problem to mitigate, making it difficult for organisations who are still wedded to the idea they can buy an appliance or service to make it go away. But a good security focused culture, along with a great data protection and modern DR approaches such as CRS are a good step in the right direct.
There is a misconception that cryptocurrencies are not traceable, but most of them are. They are actually easier to track than cash. This is why many countries are considering to transform their fiat currencies in crypto.
Almost all bitcoins paid in the Colonial Pipeline attack were tracked and recovered: https://www.nytimes.com/2021/06/09/technology/bitcoin-untraceable-pipeline-ransomware.html.