I’ve been tidying up my lab of late and when the latest version of Data Protection Central (DPC) came out,…
Introduction If an idea doesn’t get off the ground, does that automatically mean it was a bad idea? Well, no.…
A little while ago, PowerProtect Data Manager 19.10 was released. Data Manager continues to offer enhanced backup and recovery operations,…
Instant access refers to provisioning a read/write snapshot of a virtual machine backup to your VMware environment, with the storage…
A single PowerProtect DD series appliance can hold a staggering amount of backup data within your environment. The DD9900 for…
I’ve always been one of those people who has been a bit leery of mind maps. I’d see examples of…
“What happens when we die?” This is a question that has occupied countless philosophers, theologians, scientists, stoned first year university…
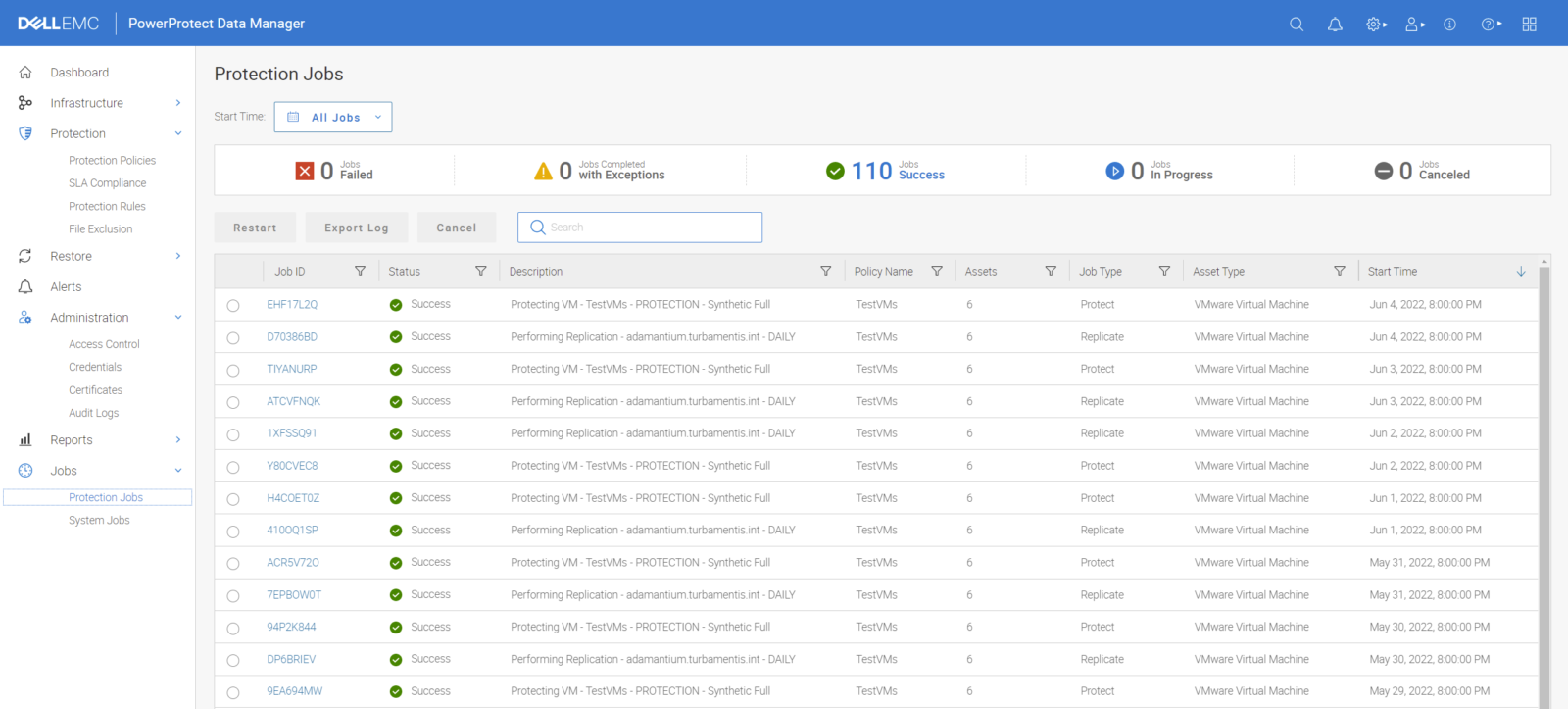
Being able to track who has done what within an enterprise data protection solution is always a useful function. It…
I recently wanted to check out some PowerProtect Data Manager options with Oracle, and so I found myself spinning up…
(This article was originally published at Musing About Tech, which I’m closing down.) Introduction When I was 16 or thereabouts…